OUSPG
[This page is CSS2 enabled. Your browser might not fully support it]
index.html,v $ $Revision: 1.58 $ $Date: 2002/12/16 13:30:45 $
WAP is a worldwide standard for providing Internet communications and
services on wireless terminals. It has been adopted in the
infrastructure of some digital mobile phone networks.
A subset of the WAP suite, namely WMLC content, was chosen as the
subject protocol and software vulnerability analysis through syntax
testing was conducted.
A survey of the related standards was made, existing implementations
were identified and targets were chosen. Test-material was prepared
and tests were carried out. Results were gathered and reported.
Many of the implementations available for evaluation failed to perform in
a robust manner under the test. Some failures had information security
implications, and should be considered as vulnerabilities.
To promote and support hardening WAP WMLC implementations this
test-material should be adopted in the evaluation and development of
these products.
This test-suite is a byproduct of the
"PROTOS - Security Testing of Protocol Implementations" project.
Important: Background, goals, limitations,
terminology and licencing for this test-suite release are explained in
the
"Test-suite releases in Theory and Practice"
document.
This test-suite covers a limited set of information security and
robustness related implementation errors for a subset of the chosen
protocol. The subject protocol and the chosen subset of it are
illustrated in the "Analysis" section below.
"WAP - The de facto worldwide standard for providing Internet communications
and advanced telephony services on digital mobile phones, pagers, personal
digital assistants and other wireless terminals."
[http://www.wapforum.org/]
"The WAP specification pulls together existing technologies and defines new
standards to provide subscribers with: ... Peace of mind that all
transactions are completely secure. ..."
[
http://www.wapforum.org/what/WAP_white_pages.pdf]
In the initial analysis the WAP suite was chosen as the focus area for
this test-suite. The factors behind this selection included:
-
WAP is a rather new family of protocols and their implementations, and
an earlier
c04-wap-wsp-request had shown us that classic vulnerabilities
still emerge in the implementations of at least one subset of the
protocol suite. Further study was deemed sensible in order to validate
this observation.
-
Reasoning made during c04-wap-wsp-request test-suite still applies.
WAP is used in critical communication infrastructure and for e-commerce.
Early scrutiny may lessen the potential financial losses.
The protocol suite was further narrowed down to one specific protocol,
namely Compiled Wireless Mark-up Language (WMLC), thus yielding protocol
data units in form of WMLC content. Rationale behind the selection:
-
Earlier c04-wap-wsp-request test-suite was aimed against server side
implementations. This test-suite attempts to address an another
important link in the chain, ie. WAP WMLC client software.
-
This area is important since WAP WMLC clients are mainly extremely
homogeneous embedded devices deployed in large quantities. Possibly
this is the first time such a vast number of potentially exploitable
installations with so little diversity have been interconnected.
-
If patch deployment for vulnerabilities in traditional client software
has proven problematic, then patching them in embedded consumer
appliances already in the hands of the customers may pose even further
challenges.
-
WAP terminals are ready to accept and process WMLC content by design.
Currently it has to arrive as a reply to a request, e.g. as the
retrieved page from a content server, or in the future (WAP 1.2)
provided as server push content.
-
WMLC was chosen over WML since it is already in compiled form and will
pass unaltered through a typical WAP gateway implementation. This is
relevant since our focus is on the terminal robustness, not on how
gateways handle compilation of WML into WMLC.
"... The company (Nokia) expects the market of Internet-enabled
handsets to reach about 60 million in 2000, of which WAP-enabled
handsets would represent approximately 40 million. For 2001, Nokia
estimates that web-enabled handset unit volumes will increase to
around 200 million with WAP handsets representing some 180 million of
the total. ..."
[
http://press.nokia.com/PR/200012/800970_5.html]
The available standards specifying the selected protocol have to be
studied, and analysed. The relevant protocol specifications are listed
in the table below.
standard-survey
| Name
| Document Date
| Organization
| Status
| Link
| Description
|
| WML
| 19990616
| WAP Forum
| Closed
| http://www.wapforum.org/
| Official WAP WML specification
|
| WBXML
| 19990616
| Wap Forum
| Closed
| http://www.wapforum.org/
| Official WAP WBXML specification
|
WMLC is basically an encoding scheme specified by WBXML (WAP Binany XML
content format) specification. The goal of WBXML is to reduce amount of data
to be transmitted by encoding XML documents into binary form. As WML
is derived from XML, WBXML rules can be applied to WML documents and the
result is WMLC document.
A survey of the available implementations is conducted. This
should include a diverse selection of implementations in order to gain
a better insight into the applications implementing the protocol, and
to give a hint of the impact of the potential
vulnerabilities. Typically, not all implementations are available for
testing, and thus cannot be tested by the project personnel within
this test-suite prerelease phase.
subject-survey
| Subject name
| License
| Platform
| Link to source
|
| Nokia 6210
| commercial
| Mobile Phone HW
| (link)
|
| Ericsson R380
| commercial
| Mobile Phone HW
| (link)
|
| Benefon Q
| commercial
| Mobile Phone HW
| (link)
|
| Siemens S35i
| commercial
| Mobile Phone HW
| (link)
|
| Siemens C35i/M35i
| commercial
| Mobile Phone HW
| (link)
|
| Motorola Timeport P.7389
| commercial
| Mobile Phone HW
| (link)
|
| Motorola Talkabout T.2288
| commercial
| Mobile Phone HW
| (link)
|
| Ericsson R320s
| commercial
| Mobile Phone HW
| (link)
|
| Ericsson 2618s
| commercial
| Mobile Phone HW
| (link)
|
| Nokia WAP Toolkit 2.0
| proprietary
| Windows
| (link)
|
| Nokia 9110i
| proprietary
| Mobile Phone HW
| (link)
|
| Phone Dot Com (OpenWave) UP.SDK
| proprietary
| Windows
| (link)
|
| Ericsson MC218
| commercial
| PDA HW
| (link)
|
| Ericsson R380 Simulator
| proprietary
| Windows
| (link)
|
| Psion 5 MX
| commercial
| PDA HW
| (link)
|
| Microsoft Mobile Explorer Emulator
| proprietary
| Windows
| (link)
|
| Opera Browser
| commercial/adware
| several
| (link)
|
| ccWAP Browser
| proprietary
| Windows
| (link)
|
| WinWAP Browser
| commercial
| Windows
| (link)
|
| Klondike WAP Browser
| proprietary
| Windows
| (link)
|
| M3Gate Browser
| proprietary
| Windows
| (link)
|
| EzWAP Browser
| commercial
| Windows
| (link)
|
| Panasonic GD93
| commercial
| Mobile Phone HW
| (link)
|
A subset of the implementations was chosen to be tested during the
test-suite creation and prerelease phases.
Note, that embedded devices from different manufacturers may contain
same outsourced implementation of a WAP browser.
The injection vector survey, or delivery vector survey, analyses the
different methods of delivering the test-cases to the implementations
under test (IUTs). Often, there are several methods of injection and
the test-suite cannot cover them all, or might miss some vectors not
available in all implementations.
injection-vector-survey
| Application protocol
| Transport protocol
| Packet
|
| WMLC+HTTP+WSP+[WTP]
| TCP+UDP
| WMLC content, in a HTTP reply converted to WSP reply over UDP by a WAP gateway
|
| WMLC+HTTP+WSP+[WTP]
| TCP+SMS
| WMLC content, in a HTTP reply converted to WSP reply over SMS by a WAP gateway
|
| WMLC+HTTP
| TCP
| WMLC content served directly in a HTTP reply
|
| WMLC+WSP+[WTP]
| UDP
| WMLC content served directly in a WSP reply
|
Each option involving Wireless Session Protocol (WSP) has choice of
using connection oriented mode (WTP) or connectionless mode.
Connection oriented (CO) mode was used if the WAP terminal supported
it, otherwise connectionless (CL) mode was used. WTP was provided by a
WAP gateway.
WTLS (Wireless Transport Layer Security) was not used for the
test-case delivery. It only affects the transport and is not
relevant when focusing on the WMLC parser implementations.
For the test-runs WMLC+HTTP+WSP+[WTP] and WMLC+HTTP delivery combinations
were chosen, first one requiring presence of a WAP gateway.
These selections for the delivery vector provided for succesful
injection against all available implementations.
Protocol data unit specifications are used as a basis for generating
the test-cases. Starting point for the design of the test-suite is to
acquire or create a machine-readable representation of the protocol
specification. The test-tool developed in this project uses a custom
dialect of BNF (Backus-Naur Form). The BNF is capable of
describing context-free syntax of a specification, but is not usually
enough for PDU generation. The specification is completed by some
semantic extensions in BNF and embedded Java-coded functions.
In this test-suite a BNF presentation of a typical WMLC document was
required. The available specifications don't specify WMLC document
structures in BNF but in XML. Thus, the specification was converted to
our dialect of BNF.
Anomalies are the changes in the normal communication packets, which
might cause undesired effects in the implementations. Some of the
anomalous cases are not malformed but follow the specification, but
might still be inputs that have mpt been considered when implementing
the software. The design of anomalous test-cases is done with the
test-tool configuration files. These anomalies aim to reveal the
undesired behaviour and do not contain any vulnerability exploits
running arbitrary code on the tested implementations, even where it
would be possible.
The following anomalies were integrated:
anomaly-details
| Name
| Category
| Selections #
| Inserted in
| Description
|
| zero_items
| -
| 1
| -
| Default case
|
| string-table
| O1
| 13
| string-table
| Overflow anomalies for first string table entry
|
| text
| O1
| 13
| text
| Overflow anomalies for text
|
| postfield-name
| O1
| 13
| postfield-name
| Overflow anomalies for postfield name
|
| postfield-value
| O1
| 13
| postfield-value
| Overflow anomalies for postfield value
|
| setvar-name
| O1
| 13
| setvar-name
| Overflow anomalies for setvar name
|
| setvar-value
| O1
| 13
| setvar-value
| Overflow anomalies for setvar value
|
| do-label
| O1
| 13
| do-label
| Overflow anomalies for do label
|
| anchor-title
| O1
| 13
| anchor-title
| Overflow anomalies for anchor title
|
| anchor-text
| O1
| 13
| anchor-text
| Overflow anomalies for anchor text
|
| a-text
| O1
| 13
| a-text
| Overflow anomalies for "a" text
|
| select-title
| O1
| 13
| select-title
| Overflow anomalies for select title
|
| select-value
| O1
| 13
| select-value
| Overflow anomalies for select value
|
| option-value
| O1
| 13
| option-value
| Overflow anomalies for option value
|
| option-title
| O1
| 13
| option-title
| Overflow anomalies for option title
|
| option-text
| O1
| 13
| option-text
| Overflow anomalies for option text
|
| fieldset-title
| O1
| 13
| fieldset-title
| Overflow anomalied for fieldset title
|
| input-text
| O1
| 13
| input-text
| Overflow anomalies for input text
|
| input-value
| O1
| 13
| input-value
| Overflow anomalies for input value
|
| input-title
| O1
| 13
| input-title
| Overflow anomalies for input title
|
| img-alt
| O1
| 13
| img-alt
| Overflow anomalies for img alt
|
| a-href-protocol
| O1
| 13
| a-href
| Overflow anomalies for a href protocol
|
| a-href-host
| O1
| 13
| a-href
| Overflow anomalies for a href host
|
| a-href-file
| O1
| 13
| a-href
| Overflow anomalies for a href file
|
| a-href-delimiter
| D
| 13
| a-href
| URL delimiter anomalies for a href delimiter
|
| go-href-protocol
| O1
| 13
| go-href
| Overflow anomalies for go href protocol
|
| go-href-host
| O1
| 13
| go-href
| Overflow anomalies for go href host
|
| go-href-file
| O1
| 13
| go-href
| Overflow anomalies for go href file
|
| go-href-delimiter
| D
| 13
| go-href
| URL delimiter anonalies for go href delimiter
|
| img-src-protocol
| O1
| 13
| img-src
| Overflow anomalies for img src protocol
|
| img-src-host
| O1
| 13
| img-src
| Overflow anomalies for img src host
|
| img-src-file
| O1
| 13
| img-src
| Overflow anomalies for img src file
|
| img-src-delimiter
| D
| 13
| img-src
| URL delimiter anomalies for img src delimiter
|
| text-null
| O2+N
| 4
| text
| Overflow anomalies for text w/o NULL
|
| postfield-name-null
| O2+N
| 4
| postfield-name
| Overflow anomalies for postfield name w/o NULL
|
| postfield-value-null
| O2+N
| 4
| postfield-value
| Overflow anomalies for postfield value w/o NULL
|
| setvar-name-null
| O2+N
| 4
| setvar-name
| Overflow anomalies for setvar name w/o NULL
|
| setvar-value-null
| O2+N
| 4
| setvar-value
| Overflow anomalies for setvar value w/o NULL
|
| do-label-null
| O2+N
| 4
| do-label
| Overflow anomalies for do label w/o NULL
|
| anchor-title-null
| O2+N
| 4
| anchor-title
| Overflow anomalies for anchor title w/o NULL
|
| anchor-text-null
| O2+N
| 4
| anchor-text
| Overflow anomalies for anchor text w/o NULL
|
| a-text-null
| O2+N
| 4
| a-text
| Overflow anomalies for "a" text w/o NULL
|
| select-title-null
| O2+N
| 4
| select-title
| Overflow anomalies for select title w/o NULL
|
| select-value-null
| O2+N
| 4
| select-value
| Overflow anomalies for select value w/o NULL
|
| option-value-null
| O2+N
| 4
| option-value
| Overflow anomalies for option value w/o NULL
|
| option-title-null
| O2+N
| 4
| option-title
| Overflow anomalies for option title w/o NULL
|
| option-text-null
| O2+N
| 4
| option-text
| Overflow anomalies for option text w/o NULL
|
| fieldset-title-null
| O2+N
| 4
| fieldset-title
| Overflow anomalied for fieldset title w/o NULL
|
| input-text-null
| O2+N
| 4
| input-text
| Overflow anomalies for input text w/o NULL
|
| input-value-null
| O2+N
| 4
| input-value
| Overflow anomalies for input value w/o NULL
|
| input-title-null
| O2+N
| 4
| input-title
| Overflow anomalies for input title w/o NULL
|
| img-alt-null
| O2+N
| 4
| img-alt
| Overflow anomalies for img alt w/o NULL
|
| a-href-protocol-null
| O2+N
| 4
| a-href
| Overflow anomalies for a href protocol w/o NULL
|
| a-href-host-null
| O2+N
| 4
| a-href
| Overflow anomalies for a href host w/o NULL
|
| a-href-file-null
| O2+N
| 4
| a-href
| Overflow anomalies for a href file w/o NULL
|
| go-href-protocol-null
| O2+N
| 4
| go-href
| Overflow anomalies for go href protocol w/o NULL
|
| go-href-host-null
| O2+N
| 4
| go-href
| Overflow anomalies for go href host w/o NULL
|
| go-href-file-null
| O2+N
| 4
| go-href
| Overflow anomalies for go href file w/o NULL
|
| img-src-protocol-null
| O2+N
| 4
| img-src
| Overflow anomalies for img src protocol w/o NULL
|
| img-src-host-null
| O2+N
| 4
| img-src
| Overflow anomalies for img src host w/o NULL
|
| img-src-file-null
| O2+N
| 4
| img-src
| Overflow anomalies for img src file w/o NULL
|
| string-table-length
| O1+U
| 65
| string-table
| Overflow anomalies for string table with invalid length values
|
| text-ste
| O2+U
| 20
| text
| Overflow anomalies for text w/ string table lookup anomalies
|
| postfield-name-ste
| O2+U
| 20
| postfield-name
| Overflow anomalies for postfield name w/ string table lookup anomalies
|
| postfield-value-ste
| O2+U
| 20
| postfield-value
| Overflow anomalies for postfield value w/ string table lookup anomalies
|
| setvar-name-ste
| O2+U
| 20
| setvar-name
| Overflow anomalies for setvar name w/ string table lookup anomalies
|
| setvar-value-ste
| O2+U
| 20
| setvar-value
| Overflow anomalies for setvar value w/ string table lookup anomalies
|
| do-label-ste
| O2+U
| 20
| do-label
| Overflow anomalies for do label w/ string table lookup anomalies
|
| anchor-title-ste
| O2+U
| 20
| anchor-title
| Overflow anomalies for anchor title w/ string table lookup anomalies
|
| anchor-text-ste
| O2+U
| 20
| anchor-text
| Overflow anomalies for anchor text w/ string table lookup anomalies
|
| a-text-ste
| O2+U
| 20
| a-text
| Overflow anomalies for "a" text w/ string table lookup anomalies
|
| select-title-ste
| O2+U
| 20
| select-title
| Overflow anomalies for select title w/ string table lookup anomalies
|
| select-value-ste
| O2+U
| 20
| select-value
| Overflow anomalies for select value w/ string table lookup anomalies
|
| option-value-ste
| O2+U
| 20
| option-value
| Overflow anomalies for option value w/ string table lookup anomalies
|
| option-title-ste
| O2+U
| 20
| option-title
| Overflow anomalies for option title w/ string table lookup anomalies
|
| option-text-ste
| O2+U
| 20
| option-text
| Overflow anomalies for option text w/ string table lookup anomalies
|
| fieldset-title-ste
| O2+U
| 20
| fieldset-title
| Overflow anomalied for fieldset title w/ string table lookup anomalies
|
| input-text-ste
| O2+U
| 20
| input-text
| Overflow anomalies for input text w/ string table lookup anomalies
|
| input-value-ste
| O2+U
| 20
| input-value
| Overflow anomalies for input value w/ string table lookup anomalies
|
| input-title-ste
| O2+U
| 20
| input-title
| Overflow anomalies for input title w/ string table lookup anomalies
|
| img-alt-ste
| O2+U
| 20
| img-alt
| Overflow anomalies for img alt w/ string table lookup anomalies
|
| a-href-url-ste
| O2+U
| 20
| a-href
| Overflow anomalies for a href w/ string table lookup anomalies
|
| go-href-url-ste
| O2+U
| 20
| go-href
| Overflow anomalies for go href w/ string table lookup anomalies
|
| img-src-url-ste
| O2+U
| 20
| img-src
| Overflow anomalies for img src w/ string table lookup anomalies
|
Legend:
-
Category column describes what kind of anomalies are integrated in the
test group.
-
Selections column describes how many test-cases belong to the test group.
-
See the table below for explanation of different anomaly types.
anomaly-categories
| Name
| Description
|
| O1
| Overflow anomaly
|
| D
| Malformed URL delimiter
|
| O2
| Reduced overflow anomaly
|
| U
| mb_uint_32 anomaly
|
| N
| Null-termination anomaly
|
The injectors implement the chosen delivery vector. Suitable injectors
already integrated in the test-tool framework were reused.
Test-run automatisation was desired due to large number of test-cases
and manual labour required to instruct the browsers to fetch all the
test-cases. This goal was achieved through the WMLC timer
attribute. Each WMLC deck (test-case) was given a timeout of one
second. After the timer expires, subject performs WSP GET request ad
receives the next test-case. However, this might not always work
because the subject sometimes is unable to parse the WMLC deck it
fetched. In those cases manual "refresh/reload" operation is required
to fetch the next test-case.
In this test-suite the WMLC content is injected as a HTTP reply over
TCP. When possible the WAP browser under test was configured to fetch
the content directly. In the typical cases (mobile phone hardware) a
WAP gateway was required to act as an intermediate converting HTTP
reply into WSP reply. See the figure below for conceptual
illustration of the injection vectors (A, B and C alternatives).
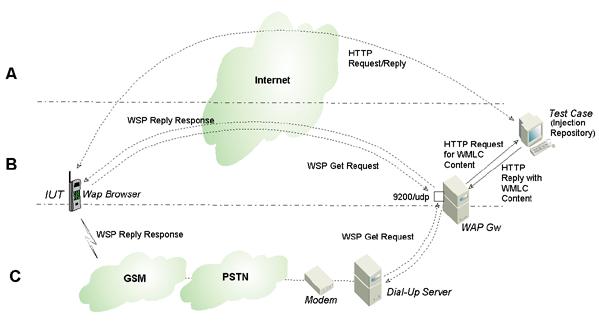
Figure: Injection vectors illustrated
Corresponding ServerSocket injector code was utilised and it acted as
a HTTP server providing WMLC content.
With instrumentation on the target platform we are able to monitor for
undesired behavior of the subject implementation. Typically this
manifests as exceptions or signals such 'access violation' and
'segmentation fault'.
No instrumentation will be bundled with this test-suite release.
Observing any undesired behavior relies solely on the tools and
logging provided by the target platform. Unfortunately the modern
trend of abusing the try-catch -type of constructs easily
masks the exceptions generated by stack and memory
corruption. Catching these hidden exceptions relies on the debugging
skills of the developers themselves.
Test-runs were conducted against the chosen subject implementations.
Packet specifications, desired anomalies, injectors and
instrumentation were integrated as a test-tool configuration to enable
automatic execution of the tests.
NOTE: The results were collected by using the prerelease 1 version of
the injector. Value of zero (which is default) for the '-closedelay
<millisec>' parameter for the prerelease 2 JAR should correspond to
the prerelease 1 test results. Try the latest test-material package
also with different values for the close delay.
Results from the test-runs are summarised herein. Tables below
represent the observations from feeding the test-material against
chosen subject software. Product names of the actual subjects are
omitted to protect the innocent. Results are presented in a tabular
form with test-cases divided into subgroups based on the anomaly
types utilised and PDU fields under examination.
testrun-data
| Name
| tr-001
| tr-002
| tr-003
| tr-004
| tr-005
| tr-006
| tr-007
| tr-008
| tr-009
| tr-010
|
| zero_items
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| string-table
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| text
| -
| X
| -
| -
| -
| -
| -
| -
| -
| -
|
| postfield-name
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| postfield-value
| -
| X
| -
| -
| -
| -
| -
| -
| -
| -
|
| setvar-name
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| setvar-value
| -
| X
| -
| -
| -
| -
| -
| -
| -
| -
|
| do-label
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| anchor-title
| -
| X
| X
| -
| -
| -
| -
| -
| -
| -
|
| anchor-text
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| a-text
| -
| X
| -
| -
| -
| -
| -
| -
| -
| -
|
| select-title
| -
| X
| -
| -
| -
| -
| -
| E
| -
| -
|
| select-value
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| option-value
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| option-title
| -
| X
| -
| X
| -
| -
| -
| -
| -
| -
|
| option-text
| -
| X
| -
| -
| -
| -
| -
| -
| -
| -
|
| fieldset-title
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| input-text
| -
| X
| -
| -
| -
| -
| -
| -
| -
| S
|
| input-value
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| input-title
| -
| -
| -
| -
| -
| -
| -
| S
| -
| -
|
| img-alt
| -
| X
| -
| -
| -
| -
| -
| S
| -
| S
|
| a-href-protocol
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| a-href-host
| -
| X
| -
| -
| -
| -
| -
| -
| -
| -
|
| a-href-file
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| a-href-delimiter
| -
| X
| -
| -
| -
| -
| -
| -
| -
| -
|
| go-href-protocol
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| go-href-host
| -
| X
| -
| -
| -
| -
| -
| -
| -
| -
|
| go-href-file
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| go-href-delimiter
| -
| X
| -
| -
| -
| -
| -
| -
| -
| -
|
| img-src-protocol
| -
| X
| -
| -
| -
| -
| -
| -
| -
| X
|
| img-src-host
| -
| X
| -
| -
| -
| -
| -
| -
| -
| X
|
| img-src-file
| -
| X
| -
| -
| -
| -
| X
| -
| -
| X
|
| img-src-delimiter
| -
| X
| -
| -
| -
| -
| -
| -
| -
| -
|
| text-null
| -
| -
| -
| -
| -
| -
| -
| -
| -
| S
|
| postfield-name-null
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| postfield-value-null
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| setvar-name-null
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| setvar-value-null
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| do-label-null
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| anchor-title-null
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| anchor-text-null
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| a-text-null
| -
| -
| -
| -
| -
| -
| -
| -
| -
| S
|
| select-title-null
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| select-value-null
| X
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| option-value-null
| -
| -
| -
| -
| -
| H
| -
| -
| -
| -
|
| option-title-null
| X
| X
| -
| -
| X
| XH
| -
| -
| -
| -
|
| option-text-null
| -
| -
| -
| -
| -
| -
| -
| -
| -
| S
|
| fieldset-title-null
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| input-text-null
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| input-value-null
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| input-title-null
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| img-alt-null
| -
| -
| -
| -
| -
| -
| -
| -
| -
| S
|
| a-href-protocol-null
| -
| -
| -
| -
| -
| -
| -
| X
| -
| -
|
| a-href-host-null
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| a-href-file-null
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| go-href-protocol-null
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| go-href-host-null
| -
| X
| -
| -
| -
| -
| -
| -
| -
| -
|
| go-href-file-null
| -
| -
| -
| -
| -
| -
| -
| -
| -
| -
|
| img-src-protocol-null
| -
| -
| -
| -
| -
| -
| -
| -
| -
| X
|
| img-src-host-null
| -
| -
| -
| -
| -
| -
| -
| -
| -
| X
|
| img-src-file-null
| -
| -
| -
| -
| -
| -
| -
| -
| -
| X
|
| string-table-length
| -
| X
| -
| -
| XH
| X
| XEH
| XS
| X
| S
|
| text-ste
| -
| X
| -
| -
| -
| -
| -
| E
| -
| -
|
| postfield-name-ste
| -
| X
| -
| -
| -
| -
| -
| X
| -
| -
|
| postfield-value-ste
| -
| X
| -
| -
| -
| -
| -
| -
| -
| -
|
| setvar-name-ste
| -
| X
| -
| -
| -
| -
| -
| -
| -
| -
|
| setvar-value-ste
| -
| X
| -
| -
| -
| X
| -
| -
| -
| -
|
| do-label-ste
| -
| X
| -
| -
| -
| X
| -
| -
| -
| -
|
| anchor-title-ste
| -
| X
| X
| -
| -
| -
| -
| -
| -
| -
|
| anchor-text-ste
| -
| X
| -
| -
| -
| -
| -
| -
| -
| -
|
| a-text-ste
| -
| X
| -
| -
| -
| -
| -
| -
| -
| -
|
| select-title-ste
| -
| X
| -
| -
| -
| -
| -
| -
| -
| -
|
| select-value-ste
| -
| X
| -
| -
| -
| -
| -
| -
| -
| -
|
| option-value-ste
| -
| X
| -
| -
| -
| X
| -
| -
| -
| -
|
| option-title-ste
| X
| X
| -
| X
| X
| X
| -
| -
| -
| -
|
| option-text-ste
| X
| X
| -
| -
| X
| X
| -
| X
| -
| S
|
| fieldset-title-ste
| -
| X
| -
| -
| -
| -
| -
| -
| -
| -
|
| input-text-ste
| -
| X
| -
| -
| -
| -
| -
| -
| -
| -
|
| input-value-ste
| -
| X
| -
| -
| -
| -
| -
| S
| -
| -
|
| input-title-ste
| -
| X
| -
| -
| -
| -
| -
| X
| -
| -
|
| img-alt-ste
| -
| X
| -
| -
| -
| -
| -
| X
| -
| S
|
| a-href-url-ste
| -
| X
| -
| -
| -
| -
| -
| -
| -
| -
|
| go-href-url-ste
| -
| X
| -
| -
| -
| -
| -
| -
| -
| -
|
| img-src-url-ste
| -
| X
| -
| -
| -
| -
| -
| -
| -
| -
|
Legend:
-
tr-nnn: Each different test-run (tr-nnn) represents a
different tested implementation.
- X: Verdict is failed - System crashed / restarted itself
- H: Verdict is failed - System hung
- E: Verdict is failed - An "effect" was seen on system before crashing
- S: Verdict is failed - WAP browser stopped working
- -: Verdict is pass - no undesired behaviour observed
The results are further summarised below.
test-results
| Test-run #
| Total test-cases
| Failed test-cases
| Total categories
| Failed categories
|
| tr-001
| 1033
| 26
| 84
| 4
|
| tr-002
| 1033
| 189
| 84
| 43
|
| tr-003
| 1033
| 8
| 84
| 2
|
| tr-004
| 1033
| 4
| 84
| 2
|
| tr-005
| 1033
| 34
| 84
| 4
|
| tr-006
| 1033
| 21
| 84
| 9
|
| tr-007
| 1033
| 25
| 84
| 2
|
| tr-008
| 1033
| 31
| 84
| 11
|
| tr-009
| 1033
| 9
| 84
| 1
|
| tr-010
| 1033
| 34
| 84
| 15
|
Each fail verdict is due to an exception, signal or unexpected
exit. Each of them represents a minimum of a denial of service type
vulnerability. In most cases they represent memory corruption, stack
corruption or other fatal error condition. Some of these may lead
exposure to typical buffer overflow exploits, allowing running of
arbitrary code or modification of the target system.
To support the vulnerability reporting process, typically one exploit
per implementation is refined and included in the respective
vulnerability report. The exploit is only intented for demonstration
purposes and is harmless as it is. The simplest of them only execute some
harmless commands in the target system, typically with the privileges
of the vulnerable process. Some only provide a demonstration by
causing a Denial of Service (DoS) against the software.
To support the vulnerability reports to the respective vendors,
following exploits were developed:
-
A buffer overflow exploit allowing execution of arbitrary code was
demonstrated for a phone similator. The implementation in
question appeared to be a cross-compilation, for the PC platform, of
the corresponding phone software. This can be taken as an indication
of the exploitability of the embedded version as well.
-
A buffer overflow exploit allowing execution of arbitrary code was
demonstrated on the PC platform for a cross-platform browser available
for phones, PDAs and PCs.
-
Denial of service exploits were demonstrated against remaining eight
WAP WMLC implementations. Some of them displaying phone corruption
that resulted in reinitialization and loss of stored data.
Test-material is distributed as a JAR-package. This package comprises
of the following elements:
-
Total of 1033 test-cases (PDUs), located in
testcases/ directory
-
Java code (source and compiled) for feeding the test-cases against
the system under test.
-
LICENSE.TXT
- GNU General Public License (GPL) version 2
-
README.TXT
- Instructions
The test-material is licenced under GNU General Public License (GPL)
version 2, at no charge. This is done in order to ensure that vendors
and their customers may freely utilise the test-material. Standard
GPL terms for no warranty and no liability apply.
We recommend some additional guidelines, although these do not
restrict the test-material licence. These guidelines can
be found from the
"Test-suite releases in Theory and Practice"
document.
Prerequisites for using the test-material are:
-
A configured WAP browser is required. (check by browsing alternative WAP content)
-
If the browser doesn't support direct HTTP then a configured WAP gateway
is required. (check by browsing through the WAP gateway)
-
Network connectivity for the browser platform, typically in cases of the
mobile phones it comes in form of a PPP dial-up to same address space where
the WAP gateway is located. (check by browsing through the WAP gateway)
The test-material can be used either with the bundled injection code
[Using with Java] or with an external
injector [Using single test-cases].
Java Runtime is a prerequisite for running the bundled Java code.
[http://java.sun.com]
This package has been tested on Java 2 SDK 1.2.2.
[http://java.sun.com/products/jdk/1.2/].
Usage examples for the injection code bundled in the JAR-package:
-
java -jar c05-wap-r1.jar -help
-
This command displays the built-in help for the available
command line options. Options such as selecting a specific
range of test-cases or non-standard destination port
are high-lighted therein.
-
java -jar c05-wap-r1.jar
-
This command activates the server mode. It starts a fake HTTP server
on the port 8000 which replies to requests for WMLC content
(test-cases). Now pointing the WAP browser to URL
http://<machine-with-jar-running>:8000 should
initiate the test-run.
The test-cases (PDUs) are in raw binary format and can be used by any
suitable delivery software, such as a WWW-server
(e.g. Apache).
The individual test-cases can be extracted from the JAR-package with
tools such as unzip, winzip or
jar. Refer to the manual pages and product documentation
of the respective tools for additional information.
After extracting test-cases you can copy them to the content directory
on your WWW-server. Note that the WWW-server must support mime-type
application/vnd.wap.wmlc. If you use Apache, adding
the following mapping into the mime.types should be
sufficient:
application/vnd.wap.wmlc wmlc
After proper WWW-server configuration you should be able to fetch WMLC
pages from your WWW-server. If your WWW-server is for example located
on 10.10.10.133, requesting URL
http://10.10.10.133/00000023.wmlc in your WAP browser
should return test-case #23.
Timer based test-run automation will not work if you are not using
the Java based injection code bundled with the test-material. This is
due to the test-cases initiating a fetch of a preset URL.
The WAP gateway utilised as part of the delivery vector while
collecting the test-results presented herein was the Kannel version
0.10.2 (http://www.kannel.org).
In prerelease 2, a parameter for setting a delay before closing the
socket was added to the injector (and thus the '-closedelay
<millisec>' parameter the prerelease 2 JAR). This was required
due to apparent asynchronous handling of closed connection
prematurately terminating the case processing in some implementations
of WMLC.
The test results are a sad reading. None of the target browsers
survived the c05-wap-wmlc test-suite. Some of the browsers survived on
WMLC that decently working WAP gateway would produce from WML, but
exceptional WMLC created in this test suite caused failures even in
these subjects.
We acknowledge the effort made by the Oulun Puhelin
(OPOY) in acquiring us hardware
implementations of the WAP browsers for evaluation.
We thank Tuukka Turunen from Nexim
Oy for providing us PDA type mobile phone test subjects for
evaluation.
Last, but not least, we are grateful to
AusCERT for their patient help,
advice and active role during the vulnerability process.
The most common sources for vulnerability information and exploits
were covered and cross checked for potential and already known
vulnerabilities in the implementations of the chosen protocol. Typical
sources for finding out about existing vulnerabilities are databases
and mailing-lists. Search-engines may also reveal information on past
vulnerabilities.
Search for already known and relevant WAP
browser vulnerabilities yielded no results.
During the prerelease phase all verified vulnerabilities were reported
to the respective vendors. The vulnerability reports are tracked by
the AusCERT in role of an
independent coordinator and advisor. An attempt is made to seek a
channel to distribute the test material to vendors whose products we
were not able to obtain for testing. A grace period of 15 months
(since Feb'2001) was kept between the vendor notification and public
release (May'2002).
Vendor statements or security advisories issued in order
to address the vulnerabilities uncovered by this test-suite
are collected. Advisories that we are aware of are listed
here-in:
[This page is CSS2 enabled. Your browser might not fully support it]
|

