|
How to Bypass Most Firewall Restrictions and Access the Internet Privately aka The Surf At Work Page |
|
|
pwc21@yahoo.com http://www.buzzsurf.com
Created: 10/25/2002 Last Updated: 8/3/2004 |
|
|
Contents
|
|
| Introduction | |
More and more employers and universities are becoming aware of the amount of time their employees
or students are spending using the Internet for personal reasons. Obviously employers want to
discourage this behavior and may implement a number of different ways to do so. These can include;
Keep in mind that the method I discuss here will protected you from NETWORK monitoring, not actual computer or keystroke monitoring. So if your IT department has some security software installed on your PC, you probably shouldn't even be looking at this page. In addition to protecting you from network monitoring, this method can be used to get around a number of other security protections that may be in place;
A couple people have asked me about this method as it relates to a VPN (Virtual Private Network). A VPN will typically let you access your work network from home, which this method can do also (to a degree). The difference is that with a VPN, your entire computer is configured like it's on your work network. So no matter what application you use, it will have a work IP address and respond just like you are at work. The method on this page just uses a proxy, so for browsing websites, it works. Anything else you want to do on your work network probably won't work. Things like telnet, mapping network drives, PCAnywhere, to name a few. You could consider this a psuedo VPN or virtual VPN. My advice however is, if you have the choice of using a VPN, always use it. |
|
| Overview | |
The objective is to encrypt your network traffic so it can not be read as it passes through your
employer or school's network. To do this, we will;
In essence, you are tricking Internet Explorer into thinking you have a proxy server running on your local machine, when in fact the proxy is running on your computer at home. Since all communication over your work network takes place through SSH, it can not be read. The SSH traffic CAN be seen, but it will look like a garbled mess of letters and numbers. Other than being a little slower than usual, you shouldn't notice any difference when surfing the web when using the secure method. Some people that are familiar with SSH and may be asking, "How can Internet Explorer talk to SSH?". Well, SSH has a great little function called Connection Forwarding. You setup SSH to accept TCP connections on a port and forward them to a port on another computer. SSH takes ALL the network traffic on that port, wraps it in a secure package, and forwards it somewhere else. I refer to this as a "shunnel"; a secure tunnel. 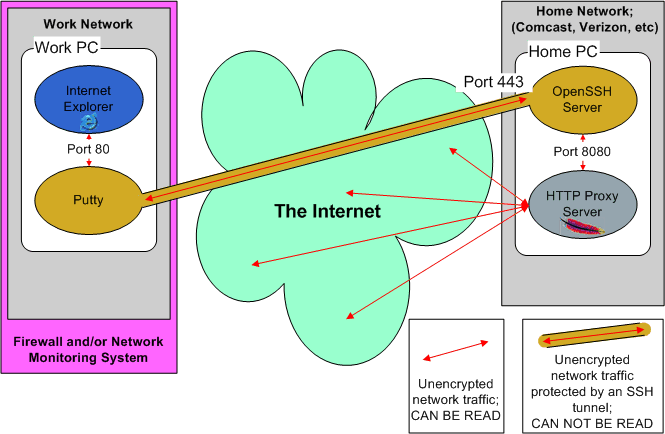
|
|
| Audience | |
|
This guide is written for a moderately skilled computer user. You MUST know how to install programs
on your computer, how to navigate file systems, and how to edit configuration files. A knowledge of
"how the Internet works", like TCP, sockets, ports, HTTP, and other network protocols
would be extremely helpful.
|
|
| Prerequisites | |
To use this method, you need the following;
|
|
| When won't this work? | |
Please notice the title of this page starts "How To Bypass Most Firewall Restrictions... I
say most because the method I describe here will not work for everyone, even if you meet the
pre-requisites above. If any of the following are true for you, you probably can't use this method
successfully;
The method I describe on this page will not work with a pessimistic blocking strategy because it depends on being able to access your home computer from work. 9 times of 10, if you can't get to www.amazon.com, you won't be able to your home computer either. If for some reason you CAN access your home computer, then great.. proceed If not, you may want to talk to your network administrator. Ask him if they would punch a hole in the firewall so you can SSH to your computer at home. Or come up with some excuse to get access to 1 port on your home computer, then run the SSH server on that port. Or... maybe you ARE the network administrator and are just curious about how this works. :) |
|
| Addresses | |
Before we start installing and configuring software, you need to find out the following things;
|
|
| Software | |
|
We're going to be using three major pieces of software; an HTTP proxy server, an SSH Server, and an
SSH Client.
Any HTTP proxy server will probably work, but I'm going discuss how to setup Apache as our proxy. Apache is the most widely used HTTP server on the Internet. It includes mod_proxy, an add in module that will allow it to function as a proxy server. It's free and secure and not too hard to setup. Download Apache for Windows from http://httpd.apache.org/download.cgi. The version I am using for this document is 2.0.47. I recommend downloading the latest version and using the .msi installer. There are a few flavors of SSH Server's out there, but we're going to be using OpenSSH because it's free. The website for OpenSSH is http://www.openssh.com. But wait! OpenSSH doesn't run on Windows unfortunately... But there is a site that converted OpenSSH to run on Windows, which is what we want! http://sshwindows.sourceforge.net/. Download OpenSSH for Windows from http://sourceforge.net/project/showfiles.php?group_id=103886&package_id=111688. The version I wrote this document using was 3.7.1p1-1. The latest version should work for you. For the SSH Client I recommend using Putty. Putty is a small single executable SSH client with the ability to setup a tunnel. It's possible to use OpenSSH as your client as well as your server, but Putty is much easier to setup and use. Download putty.exe from http://www.chiark.greenend.org.uk/~sgtatham/putty/download.html. |
|
| Install Apache | |
On your home computer, run the Apache install program you downloaded. Choose Typical Install, and
install as a service on port 80 (we'll change later). The install should ask for the following;
Note; Apache 2 includes an annoying little feature called the "Apache Monitor". It's a service that plants itself in your system tray and tells you when Apache is running. If you don't mind it, then leave it. Otherwise go into your start menu, find the "Startup" group, and delete the entry for it. After that it won't run unless you start it up yourself. |
|
| Configure Apache | |
|
Note for all Windows users! Many of the configuration files we will be editing are in native
Unix format. This means that Windows Notepad will not read them correctly. Use Wordpad instead. If
you open a Unix text file in Notepad and all the words run together on the same line, and sentences
are separated by little black boxes, that means it's in Unix format. Open it in Wordpad and it will
look normal.
|
|
|
We want to configure Apache to listen on port 8080, and we want to enable the proxy server so the
local host (and ONLY the local host) can connect and use it.
From the Start Menu run "Edit the Apache httpd.conf Configuration File" under the Apache group/Configure Apache Server. Remove the # sign in front of the following 4 lines; LoadModule proxy_module modules/mod_proxy.so LoadModule proxy_connect_module modules/mod_proxy_connect.so LoadModule proxy_http_module modules/mod_proxy_http.so LoadModule proxy_ftp_module modules/mod_proxy_ftp.so Then, change the line Listen 80 to Listen 8080 Then, find the section that looks like this: # # Controls who can get stuff from this server. # Order allow,deny Allow from all Change it to look like this: # # Controls who can get stuff from this server. # Order deny,allow Deny from all Allow from 127.0.0.1 Finally, find the line "Section 3: Virtual Hosts". Right above that line, add the following text: <IfModule mod_proxy.c>
Big fat extremely important note!
After making these changes, save httpd.conf. From the same program group in the Start Menu, run Test Configuration. If you made all the changes correctly, a black box will flash and then disappear. If you made any mistakes, a black box will appear and tell you where you screwed up. Go back and fix it. |
|
| Install SSH | |
|
The OpenSSH installer comes in a zip file. Unzip the file, then run
setup371-xxxxx.exe. The name of the file will depend on the last time they built it, and when you download it.
Choose to install both the
Client and the Server. It will ask you to install into
C:\Program Files\OpenSSH. If you choose to install into a different location, that fine,
but be aware I will use the above path in this document.
|
|
| Configure Windows | |
|
OpenSSH for Windows uses Windows' user database for login authentication. That mean you must have a User
name and Password setup to login to your home computer. If you don't, you have 2 choices. 1, set a
password on your Windows account, or 2, create a new local account that you will use to login from
SSH. I know a lot of people out there don't use logins or passwords on their home computer, but if
you're using NT, 2000, or XP, the functionality is there, even if you don't use it.
There are many different flavors of Windows, with different methods of creating a local user. There's no way I can cover all of them, but here are a few examples; To create a new account on your home machine (Windows XP):
|
|
| Configure SSH | |
|
We want to configure your SSH server to allow access using User name and Passwords, and to listen
on port 443 instead of port 22.
Why port 443 instead of port 22? In most cases your employer will block almost all outgoing network ports except for port 80 and port 443, which are the 2 ports that web servers run on. I used to tell people to run SSH on port 80 because that's the standard web server port, but now I recommend you run it on 443. Port 443 is used for encrypted websites, which is what your shunnel traffic will look like as it passes through the firewall. If you have trouble on port 443, try it on port 80 instead. If neither work, you're probably out of luck. Open Windows Explorer, navigate to C:\Program Files\OpenSSH\etc. Open the file sshd_config using Wordpad. (That's sshd_config not ssh_config!)
mkgroup -l > ..\etc\group Then mkpasswd -l > ..\etc\passwd These 2 commands will create group and password files at C:\Program File\OpenSSH\etc |
|
| Start/Stoping Apache and SSH | |
|
On your home computer, open a command prompt. To start your servers, type the following:
net start opensshd net start apache2 To stop your servers type the following: net stop opensshd net stop apache2 To make it easy, you can create a .bat file that will execute the 2 commands. If you make a shortcut to the .bat file in your Windows startup group, then when you turn on your home computer in the morning, the servers will startup automatically, and be ready for you when you get to work. |
|
| If you have a wired or wireless router at home (Linksys, D-Link, Netgear, etc) | |
|
Some routers call it port forwarding and others call it virtual servers, but the setup is very
similar no matter what brand you use. You will need to configure your router to route port 443 to
the computer where you're running the SSH server. I not going to go into details, but there is
usually a browser based interface directly to the router, which will have a page to setup virtual
servers. Configure it to forward port 443 to your SSH computer, port 443.
|
|
| Setup Putty at Work/School | |
|
Copy putty.exe to somewhere on your hard drive at work. c:\ will do fine, or anywhere else you
want. Your desktop is convenient but kind of obvious. If you don't have permissions to write files to
your hard drive, just copy putty.exe and shunnel.bat to a floppy disk or burn them onto a CD. Take
the disk to work and run Putty from the appropriate drive.
Open Notepad and copy the following into it, change the bold parts where necessary; "putty -L 80:127.0.0.1:8080 -ssh homeIP -port 443"
|
|
| Create your tunnel | |
|
At work, simply double click shunnel.bat to initiate the shunnel. A Putty window will popup asking
for a login name and password. Type the user name and password you created above on the Windows
account. If it works, you will be presented with a DOS prompt waiting for a command. This is
actually a command prompt to your HOME machine. You can use it if you want, but as long as this
command prompt is open, your tunnel is alive. To close the tunnel, type exit or close the window.
|
|
| For Advanced Users | |
|
If you are very familiar with SSH and know what you are doing, you can set this up so you don't
have to enter a password each time you create the shunnel. You have to install OpenSSH as your SSH
client and then setup key based authentication by creating a public and private key on your work
computer. Install the public key on the SSH server on your home computer. Create shunnel.bat using
this command "start "shunnel" /B "C:\Program Files\OpenSSH\bin\ssh" -l userID -c
blowfish -p 443 -C -N -2 -L 80:127.0.0.1:8080 homeIP" Thanks to Robert W. for this suggestion.
I may go into more detail on how do set this up in the future.
|
|
| Configure Internet Explorer | |
|
Now we'll configure Internet Explorer at work to use a proxy server.
First, go to http://www.whatismyip.com. Write down the number. This is your work IP address without the private connection enabled. In Internet Explorer, open the Tools menu, then click Internet Options. Click the Connections tab, then click LAN Settings. Check "Use a proxy server" and enter the following: Address: 127.0.0.1 Port: 80 Click OK. Close Internet Explorer and restart it. First, go to http://www.whatismyip.com again. If everything worked correctly, the page should have changed to show your HOME IP address, NOT your work IP address. If it shows your home IP Address, congratulation, your surfing the web securely and privately from work. |
|
| Configuring other applications to use the private connection | |
|
Most applications that access the Internet can be configure to use the shunnel. For it to work,
they have to support an HTTP proxy connection. Instant messaging programs like AIM, ICQ, Yahoo IM,
and mIRC all support this.
Setup is different for all application, but the settings will be the same. You want to configure the application to use an HTTP proxy server, Host should be 127.0.0.1, and Port should be 80. |
|
| Protect yourself from someone looking over your shoulder | |
|
Here's a great application that fits in perfectly with the theme of this page. It's called
Ghostzilla; http://www.ghostzilla.com/. The idea is that
you want to surf the web, but have it look like you are doing normal work to people walking by your
computer. Ghostzilla is a browser that hides itself in your normal work applications, like Excel,
or Word, or Visual Studio... anything. With a swish of the mouse, Ghostzilla pops up and you can
surf the web. If you see someone coming, simply move the mouse away, and it disappears, leaving no
trace. Plus, you can easily configure it to use the shunnel as described here, for total privacy!
|
|
|
Copyright © 2002-2004 BuzzSurf.com - All rights reserved. Please do not repost or retransmit the content of this page. You are welcome and encourged to link to the page. http://www.buzzsurf.com/surfatwork BY VIEWING THIS PAGE, YOU EXPRESSLY AGREE THAT ALL RISKS ASSOCIATED WITH THE METHOD DESCRIBED ABOVE IS ASSUMED SOLELY BY YOU. THE AUTHOR SHALL NOT BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL OR CONSEQUENTIAL DAMAGES ARISING OUT OF USE OF THE METHOD. THE METHOD IS MADE AVAILABLE BY THE AUTHOR "AS IS" AND "WITH ALL FAULTS". THE AUTHOR MAKES NO REPRESENTATIONS OR WARRANTIES AS TO THE TRUTH, ACCURACY OR COMPLETENESS OF ANY INFORMATION ON THIS PAGE. |
|
|
Notes: 11/21/2002 - The page is starting to pickup in popularity. I'm interested to know if anyone else has been successfully in getting it to work. Drop me an email. Thanks. 11/21/2002 - Please email me if anyone notices errors or security holes! 01/17/2003 - Changed to use Putty as an SSH Client instead of OpenSSH. Thanks to James.Q.L for this suggestion. 01/22/2003 - Added Ghostzilla blurb. 03/05/2003 - Added Amazon Honor System links to ask for donations. Check it out! 03/19/2003 - Changed theme a bit to highlight ability to bypass a firewall. Based on google searches, getting around a firewall is actually more popular than protecting privacy. 05/22/2003 - Changed recommended SSH port from 80 to 443. Should work just as well on 443 and set off less alarms because traffic on port 443 is encrypted anyway. 06/02/2003 - Chopped page up into "concept" and "description" pages. Now asking for donations to access the description page. 09/11/2003 - Added link to Amazon Wish List 09/13/2003 - Updated Apache instructions to version 2.0.47 09/25/2003 - Updated OpenSSh instructions to version 3.7.1. A security flaw was found in version 3.4 that I was previously using! All users whould upgrade to 3.7.1 or higher. 01/14/2004 - Page resurrected after being down for a few months... Server died, sorry! On temporary hosting until new server is ready. 01/22/2004 - Hosting on rebuilt server. 08/03/2004 - Updated some broken links and changed a few minor wording issues. 
|