The Comprehensive Guide to 802.11b Wireless Networks
by Dragorn
Wireless networking has been around for decades (fixed microwave links, laser links, ham packet radio), but wireless Ethernet, (a.k.a. Wi-Fi - short for "Wireless Fidelity," a.k.a. 802.11b) has recently exploded in popularity for home and office use.
As is too often the case with any new, widely adopted technology, the average consumer has little understanding of the impact of the little box with antennas that they just hooked up to their cable modem or that their office manager just told them to install on the network.
802.11b Background and Basics
802.11b is part of the 802.11 wireless family (which includes 802.11a and 802.11g, however neither are as widely used as 802.11b).
Operating in the 2.4 GHz unlicensed radio band, 802.11b is designed to offer up to 11 Mbit (closer to 6 Mbit usable) over short distances (typically less than 1,500 feet) but with custom antennas and a clear line-of-sight, links of several miles are possible.
Because it operates in the unlicensed band, no single corporation controls the airwaves. But unfortunately, this means there is also a lot of garbage floating in the 2.4 GHz range of the spectrum along with the wireless data. Many cordless phones operate in the same frequency and house-hold microwaves leak significant noise into the 2.4 GHz range.
Some wireless camera equipment (X10) uses the 2.4 GHz range as well. WLANs also recently faced the threat of severely restricted transmission power due to a petition by Sirius satellite radio, however the complaint was recently withdrawn by the company.
802.11b operates in two modes - infrastructure, where dedicated Access Points (APs) act as the central points for a large number of clients and ad-hoc, where each client talks directly to other clients.
In infrastructure mode, each client needs only to be able to see the AP (or another AP in the same distribution system) - two clients need not see each other directly because the AP will relay traffic.
In ad-hoc, every client must be in range of every other client. In either operational mode, it is, by definition, a shared media network - everyone can see all the traffic in the air or, at least, all the traffic in the air that they are in range of.
Each 802.11 b network is given a Service Set Identifier, or SSID. This is the name of the network, which all clients use to identify which network they are communicating with. Networks operate on one of 12 (in the U.S.) or 14 (international) channels. Most wireless setups will automatically select the best signal out of all the network points sharing the same SSID.
802.11b has link-layer encryption called Wired Equivalence Protection, or WEP. WEP uses RC4 in 40-, 64-, 128-, or on some recent cards, 256-bit encryption. While never designed to provide a tremendous amount of security (wired equivalence implying "as secure as a shared media wired network," which, as anyone running a sniffer on a wired shared media network can tell you, isn't very secure), additional flaws have been found in WEP which allow key attacks against data encrypted by many manufacturers. More on this later.
802.11b Packet Types
The most common types of 802.11b packets are:
- Beacon Packets: Typically, access points continually transmit beacon packets containing their SSID, maximum transfer rate, and MAC address of the access point. Most APs send between six and ten beacon packets a second continually. Although some newer APs allow the user to disable this feature.
- Probe Packets: When a client tries to join a network it sends a probe request packet containing the SSID of the network it wishes to join. If an access point allows the client to associate with the network, it responds with a probe response, also containing the SSID.
- Data Packets: Typically, these are just TCP/IP encapsulated in the 802.11 frames.
- Ad-Hoc Packets: These are no different than data packets except they are sent card to card instead of through an access point.
Detecting 802.11b Networks
There are two primary methods for detecting wireless networks, utilized by different programs:
- Active Detection: Where the client transmits probe requests and looks for networks that respond to them.
Positive: Sometimes able to detect cloaked networks, does not require a card or driver capable of RF Monitor support.
Negative: Requires the client to be within transmit range of the access point for it to be detected, generates traffic on the target network which can be traced, and lies on questionable legal ground so far as actively joining a network is concerned.
Used By: NetStumbler.- Passive Detection: Where the client listens to all wireless traffic in the air and extracts information from the packets found.
Positive: Client needs only to be within receive range to detect a network, no traffic is generated which can be observed. Passive sniffers are also capable of recording data packets for additional dissection.
Negative: Requires a card and driver capable of RF Monitor support, which enables raw packet detection. Cannot detect a non-beaconing network with no data traffic.
Used By: Kismet (www.kismetwireless.net), Wellenreiter (www.remote-exploit.org), Airsnort (airsnort.shmoo.com)
Using passive sniffing it is essentially impossible to detect someone monitoring your network. No traffic is generated by the sniffer and, even in "secure" environments, a handheld such as the iPAQ or Zaurus are more than capable of capturing traffic and can easily be kept in a jacket pocket or bag.
Passive monitoring of wireless data opens many advantages for tracking and analyzing networks. The level of monitoring possible varies depending on the type of card used.
Cisco cards use a very fast hardware channel hopping method, which allows them to scan all of the channels transparently. PRISM2 cards must do channel hopping to detect all the 802.11b channels, spending a small amount of time on each channel - most wireless sniffers include this capability either internally or as a helper application (Kismet uses prism2_hopper to hop three channels per second).
The most simplistic information is in the 802.11b headers - the MAC of the source, destination, and access point systems, the direction of communication, the channel, SSID, WEP, and supported transfer rates. Cisco access points even include an extra status field that often contains information about the function of the equipment, and sometimes even the location of the wireless access point.
Far more information can be gathered by dissecting the data packets of unencrypted networks - FTP, Telnet, HTTP, POP, and IMAP traffic are all as vulnerable to observation as they would be in an unswitched Ethernet network. ARP, UDP, and especially DHCP can be used to detect the IP ranges used by the network.
Basic sniffing can be done with almost any wireless card, but some are better than others.
Most consumer wireless cards are underpowered, only capable of detecting strong signals, and don't support external antennas. ORiNOCO cards are more powerful than most, and support antennas, however it is not always possible to do full RF Monitor mode, which is required for passive monitoring (there are patches to the Linux ORiNOCO drivers but they only work on some firmware versions).
While not perfect, one of the best cards for general sniffing is the Cisco AIR-LMC350 which has dual-antenna jacks, 100 mW transmit, and -95 dBm sensitivity (compared to 20-30 mW transmit for most PRISM2 cards and -80 dBm sensitivity).
As mentioned before, the Cisco chipset uses a very fast internal channel hopping scheme, which can sometimes result in missed packets if a single channel is saturated, but overall the performance of the card is excellent. It can be obtained through online retailers for approximately $110 US.
Equally important is a proper antenna - remember that a car is just a big metal box, and metal boxes are not good for radio signals. A car-mounted antenna, while not absolutely necessary, will often triple the amount of data received. 5 dB gain magnetic-mount antennas can usually be found for $60 U.S.
The Myth (and truth) of WEP, SSID Cloaking, and Non-Beaconing
WEP is alternately touted as the only protection you'll ever need, and so weak it's not worth enabling.
The truth lies, as always, somewhere in the middle - all, or nearly all, modern chipsets include workarounds for the flaws in WEP key generation, however all it takes is a single older system on your network (access point or client) to expose the key.
WEP only encrypts data packets - link layer packets such as joining, beaching, probes, etc. are left unencrypted. Actually cracking the WEP key depends on the key length, the number of flawed systems generating traffic, and the traffic levels on the network - if there are no systems generating data traffic, you will never have the opportunity to capture weak keys. The most important factor is time - typically only one or two in thousands of packets contains a weak key, and current key attacks require thousands of weak keys to extract the full key.
Various dictionary-based brute-force attacks are under development, but will of course have the same weakness of any brute-force attach - beyond the expected range of likely keys it becomes time consuming number crunching.
WEP has the additional flaw or being a shared private-key encryption method.
Once your key is cracked (or otherwise compromised by system being cracked, insecure means of giving the key to personnel or other network users, and employee leaving, or even an employee losing a wireless-enabled handheld), all systems must be updated with a new WEP key, which has the same weaknesses and vulnerabilities as the previous one.
Coupled with additional security (as discussed later), WEP can be a useful deterrent, however it is by no means sufficient as the only life of defense - while it may foil the casual sniffer, a determined attacker with the right tools stands a god chance of breaching your network.
In a further attempt to make consumer hardware more secure, or to at least appear more secure, many manufacturers include SSID "cloaking," where the SSID is blanked from the beacon packets. Unless a client knows the correct SSID, it cannot join the network. Unfortunately, this "protection" is completely transparent - once a client joins the network, the SSID is sent by the client and the AP in clear text (even if WEP is enabled - remember, WEP only encrypts data packets, not link packets).
Kismet automatically detects this exchange and fills in the network SSID. If you have users on your network, your SSID will be exposed.
Several physical attacks (of varying legality) are possible to force a cloaked network to disclose the SSID - when a card gets a weak signal or loses the signal, it attempts to rejoin the network, disclosing the SSID. Any 2.4 GHz RF interference strong enough to disrupt the network and cause systems to rejoin will, in addition to being against all FCC regulations, happily cause a disclosure of the SSID.
The second common trick favored by manufacturers to try to protect AP's is to disable beaconing entirely. While not completely in accordance with the 802.11b specifications, this doesn't cause major problems for normal operation. However this, like SSID cloaking, does not provide any significant protection. Any data traveling over the network can still be seen, and the SSID is disclosed in the same fashion as the cloaked SSID by users joining the network.
Securing Wireless Networks
After all of the above doom and gloom, how docs one secure a wireless network?
There are two primary methods that can be used, and are most effective when used in conjunction:
- Application or network-layer encryption. This can be as simple as SSH (or an SSH-tunneled PPP virtual network) or as complex as IPsec,
- Proper authentication. MAC addresses can be easily spoofed. Some APs offer enhanced login authentication (Cisco LEAP). For APs that don't (most consumer equipment), solutions like NoCat (www.nocat.net) can provide secure authentication methods to protect the rest of your network from the wireless segment.
- Properly tuned equipment. Don't assume stronger is better! Always use the minimum power possible for your network and select your antennas appropriately. Not only is it good for security, this will help reduce the congestion in the 2.4 GHz band.
Community Wireless Networks
Wireless networks provide a phenomenal level of networking possibilities.
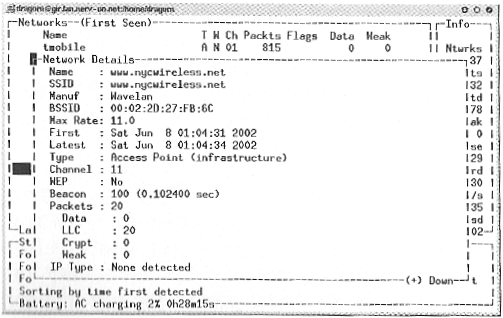
Most urban areas have at least one wireless users' group aimed at building a free, community wireless network. Often called a wireless mesh or a parasitic grid, community networks aim at blanketing a city (or parts of a city) with free broadband access. Groups such as NYCWireless (www.nycwireless.net, New York City, NY), BAWIA (www.bawia.net, Boston, MA) and Personal-Telco (www.personaltelco.net) have already made significant inroads into providing wireless public networks.
Community wireless networks offer an alternative to "big business" broadband and can often get broadband to areas unreachable by conventional means, and can provide a completely independent means of transport for free information without relying on any corporate services or resources. After September 11, the NYCWireless group was involved in bringing back connectivity to areas left without links that the large providers had not been able to restore.
While uncommon, sometimes companies (knowingly) share their wireless networks. Akamai in Boston allows public use of their wireless network equipment, which covers most of Cambridge, with minimal filtering of outgoing traffic (SSH and HTTP both work fine).
In most cases, donating a node to a community network is as simple as putting an access point on a broadband connection (cable, DSL, or other) with a public SSID and registering it with the group of your choice. The web site for a wireless group in your area should contain all the information you need to join.
Threats to 802.11b
802.11b in general and community networks specifically face several hurdles in the near future.
Broadband companies are beginning to crack down on the sharing of access and on users who utilize the full bandwidth allocated to them. Connection sharing is already against the acceptable use agreements of most broadband providers, and not far away for most others, and should providers begin charging per megabyte over an arbitrary quota (as Time Warner Road Runner is considering), free public broadband could quickly become a thing of the past.
Also, in many urban areas (and even less urban areas) the airspace available for wireless networks is becoming saturated. Just like collisions in shared-media Ethernet, as more wireless networks with overlapping signals are in an area, less bandwidth is available for each. Non-802.11b devices like phones, microwaves, cameras, and even a planned microwave-based lighting system all leak noise into the air that further degrades 802.11 b signals.
Finally, while the current 802.11b equipment is well understood and supported with open-source drivers, manufacturers are aggressively discouraging community-developed drivers for 802.11a hardware, and in fact as of the time of this writing it is completely unsupported in Linux.
Practical Examples
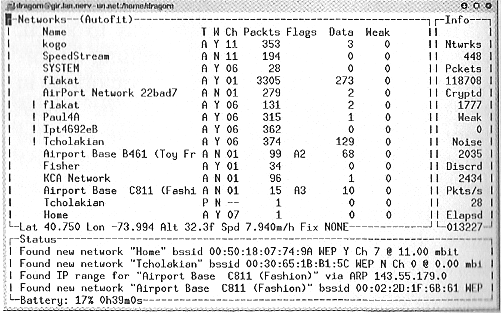
To gather the data for the cover we used a Cisco card, mag-mount antenna on the roof, a Garmin GPS, and Kismet.
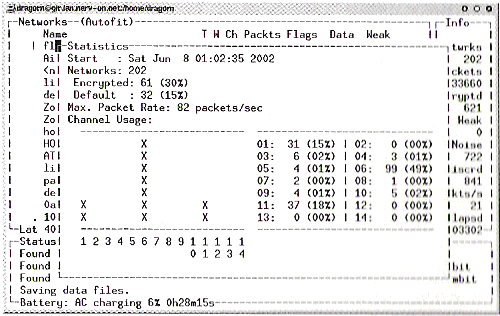
In an hour and a half, we found 448 networks. In the center of Manhattan, an area which arguably should be more security aware than anywhere else, only 26 percent of the networks had encryption enabled. At least 75 of the access points were factory configurations, with all the default access granted.
Plaintext data included searches on outpost.com, an individual with 129 email messages (every single one of them porn spam), books purchased at Barnes & Noble, IRC sessions, instant messenger conversations, browsing at the Fry's website, Windows Network Neighborhood file transfers, data from globix.net, uPNP services looking for drivers, and more.
Vulnerable networks ranged from personal systems in apartments, law firms, bookstores, and news companies. At the very least they exposed all of the data handled by the company, and at the worst presented an easy entrance into the corporate network.
Wireless demo units are often plugged in behind the corporate firewalls of retail stores (Office Depot for months ran a default Linksys demo unit plugged into the corporate network behind the firewall).
Books Processed at Barnes & Noble During the June 7, 2002 2600 Meeting
Good Old Coney Island, Ingram Book Company, $19.95 Times Square Roulette, MIT Press, $59.95 Art of the State: New York, Abrams, Harry H. Inc, $12.95 AIA Architectural Guide, $14.95 New York Design Index, Norton Publishing, $59.95 New York's Architects, $12.95 Stone and Steel : Paintings & Writings Celebrating the Bridges of New York City, Baker & Taylor, $30.00 NY Yankees Collection, Ingram Book Company, $24.95 When the Tripods Came, Simon and Schuster, $4.99 Pool of Fire, Simon and Schuster, $4.99 City of Gold and Lead, Simon and Schuster, $4.99 White Mountains, Simon and Schuster, $4.99 Rainbow Jordan, Harper Collins, $4.99 Extreme Teen Bible Just A Future With A Promise, Thomas Nelson Inc, $19.99 Rise of New York, Yale University Press, $30.00 Long Island Country, Norton Publishing, $85.00 The Rockefeller Family, Abbeville Press Inc, $49.95 Truth or Dairy, Harper Collins, $6.95 Wurst Case Scenario, Harper Collins, $6.95 My So-called Life, Random House, $4.99 Chernowitz!, Penguin/Putnam Paper, $5.99 Where the Lilies Bloom, Harper Collins, $5.95 Children of the River, Random House Inc, $5.99 Athletic Shorts: Six, Random House Inc, $4.99 Drifter, Simon and Schuster, $3.99 Stotan!, Random House Inc, $4.99 Ironman, Random House Inc, $4.99 Crazy Horse Electric, Random House Inc, $4.99 Old Magic, Simon and Schuster, $4.99 Watsons Go To Bermin, Random House Inc, $5.99 Neon Genesis Evangelion, Publishers Group West, $15.95 Star Wars: Dark Empires, LPC Group, $17.95 Gift of Magic, Random House Inc, $4.99 |
Wireless Networks Found in Midtown Manhattan
See PDF |