ValuePoint
by by Sidge.2 & Bimmerfan
As some of you may know, the company ValuePoint sells wireless access points to some of the biggest hotel chains in America.
This includes Best Western, Choice Hotels, Hampton Inn, Hilton Hotels, Holiday Inn, Marriott, Ramada Inn, and many other subsidiaries as well as independent access points and hotels around the world.
From www.valuepointnet.com:
ValuePoint Networks supports hundreds of service and solution providers worldwide by providing a complete line of rugged, powerful, and highly reliable wireless products designed with the solution provider in mind. Simply put, ValuePoint's products do the job the others cannot, and for a price the others cannot match.
Founded in 2002 to develop products designed specifically for hotspots and other public access venues, ValuePoint has quickly become a leader in this burgeoning space, and has expanded into other markets as well, such as industrial, WISP, MTU/MDU, and municipalities.
With Rugged Access Points and Advanced Gateway Controllers, shipping since early 2003, ValuePoint Networks' products are deployed today in thousands of venues around the world.
Hotels, marinas, shopping malls, RV parks, MTUs, MDUs, and virtually every imaginable location are operated using ValuePoint Networks' renowned SuperAP, MultiAP, SuperMesh, and Gateway Controller products. ValuePoint offers our Customers superior solutions at much lower price points, thereby minimizing your up-front capital investment.
Recently I stayed at the America's Best Value Inn in Las Vegas.
We stayed there because it was cheap, near the monorail, and they offered "Free Wi-Fi." I won't give a hotel review. We paid for a cheap hotel and that's what we got. But, if someone advertises free Wi-Fi they should deliver. The Wi-Fi connection was shoddy at best and halfway through the second day it stopped working completely: We decided to investigate.
When you first attempt to connect to any web page you are redirected to the Terms of Service (TOS) page.
The page is at IP address 1.1.1.1 but also resolves on 192.168.0.1.
I loaded: http://192.168.0.1/html/index.html
The HTML structure was what enabled us to find all of the information to hijack the box. My first idea was a basic one - just look at the login form and see where it was submitting:
So I did what any halfway intelligent person would do:
The frame source for the login screen was far more interesting than I had previously expected.
It turns out that ValuePoint's security setup is mostly done in JavaScript. This goes for their pageloads as well.
Upon examining the source for the left column I found something fairly interesting:
It appears that there are three windows that open.
This site uses frames and the JavaScript simply overwrites the current frame with the new HTML. The problem is that as_system.html in the main frame finds nothing.
So I did the next best thing and loaded the menu_as.html. It worked like a charm and actually loaded. The menu it loaded was the preloaded and highlighted Advanced Settings menu.
After browsing through several options and finding only a few that seemed to do anything, we clicked on the Apply Settings button at the bottom and then clicked that it was O.K. to reboot.
The ping routine we were doing on a separate computer stopped. Even logged out, the reboot routine worked.
After the server rebooted, I decided to try the only other button I hadn't tried. It appeared to bring up a file called sitemap.html.
I clicked on it and it brought up three new windows. This was the key. I tested this in two browsers on my Mac. It did not work in Firefox but it did work in Safari.
This is the sitemap and for navigating this system in one frame I couldn't find anything better.
Now at this point, we're in the back end of the system and can get to anything and change anything. The problem is that there are a few steps for every change and I really) wanted to get the same view as the administrators.
So we decided to see if we could find out what the administrator password was. So we browsed through and clicked on Admin:
After you click a link you are greeted with this message on top of the opening "Terms of Service" agreement page.
The reason this hack works is because of an insecurity in the Java code that authenticates. It loads the correct page and then checks to see if you are an authentic user. If you are not authenticated it loads the TOS into the mainframe overwriting the information that you want to get.
By loading this in separate windows you bypass the ability to perform this specific action.
In Safari, the window with the error message loads in a new page leaving the data untouched and open. This enables you to see anything that you want.
Now, as I said, this is easy. But for me, it's always easier to find a username and password so that I can really see what the managers see.
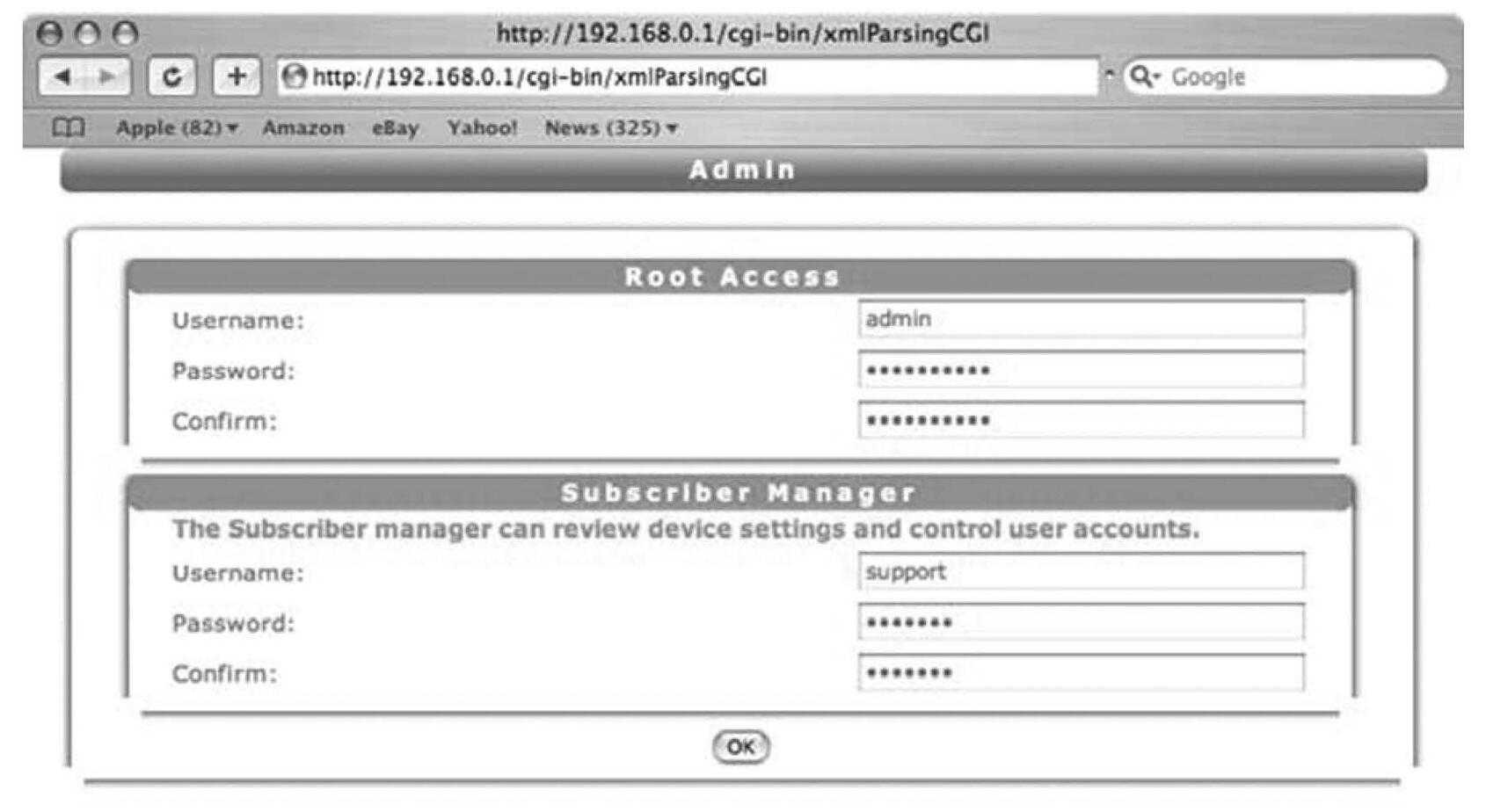
So we navigated to the admin page under the System Tools:
Under the window that I closed I saw this.
It is the admin page and contains the username and password fields for both root and subscriber manager privileges. I expected at least MD5 encryption but we figured since the rest of the system was so poorly made we would check. So we did the easiest thing we could think of.
It couldn't be this easy though, could it?
Sadly, yes. It was this easy. We ascertained the user and password and the only thing left to do was to give it a try:
And there we have it.
We now have complete control over our motel's network. We can change whatever we want including Terms of Service and the forwarding page.
Or we could change the login page information. Basically anything we wanted.
Sadly, we were unable to fix the server. Oh well, maybe next time.
For now we just left some information on how we got in and then we got out of there. This is by far the easiest intrusion attack that I've ever done and on one of the most widely available nationwide systems.
It just goes to show you that if you are involved in a business that always buys the cheapest gear you should expect to get broken into. Sometimes it is better in the long run to spend a little money in order to prevent fraud on your system.
There is no reason that I couldn't have changed the Terms of Service page into a credit card validation page where a hotel member enters their number and name and security code with a disclaimer saying "The Ethernet is free but we must verify your credit card number to that on your room to confirm that you are staying at our hotel."
How many cards could we have gotten before they figured it out? For anyone using this system: Find another system.
Breaking this one took all of ten minutes. It is not worth the hassle to your customers and your security.