The Importance of Updating Your Computer and Hacking Your School's Network
by Desert_Fox and 6|21|3|11
As all of you know, especially Windows users, one of the most essential things that you should do to protect your computer is install weekly or monthly updates. That is probably one of the most well-stressed pieces of advice that any frequent computer user should take to heart, and we've got a great example as to why.
For three months, 6|21|3|11 and I were extremely curious about exactly how secure our school's network was. We aren't going to tell you what school it was, mainly for security reasons and because our administrators would probably send us to jail if they were to find out. Also, I believe that there's at least one student out there who goes to our school and would love this information. All we're going to say is that it's a big high school, somewhere in the western U.S.
I'm sure that everyone remembers the MS Blaster Worm and all the security warnings about the RPC DCOM vulnerability. While I still don't know exactly what the RPC DCOM does, probably because I'm too lazy to look it up, there are some quick things that I know about it. First, it runs on port 135, but ports 139 and 445 are vulnerable as well, and it is on by default.
Second, the vulnerability affects unpatched Windows 2000, XP, and Server 2003 installations.
Third, once exploited you can gain complete access to the PC through the command prompt and have full privileges, depending on which user is currently logged in. And lastly, MS Blaster infected over 500,000 PCs whose owners failed to update their computers through Windows Update and then tried to use the infected PCs to DDoS the Windows Update website, but failed at that because the URL that was coded in the worm was actually just a mirror to the site, which MS took offline (damn that sucks).
O.K., so after that vulnerability came out and even before the MS Blaster worm came out, there was a whole mess of exploits all over the Internet. School was just about to start and I had a computer graphics class with 6|21|3|11 and we spent most of the time in class trying different programs to see if we could crack the admin password on our computers, which were running Windows 2000. Well, we failed at that because, unfortunately, the computers were updated.
We had a little fun with CGI proxies throughout the month of September, when we found out that they bypassed the school's Internet filter, but eventually the admins caught up to us and blocked every CGI proxy that could be used. By the way, it took me five minutes to figure out how to bypass the filter. I actually typed [How to Bypass Internet Filters] into Yahoo! and then got through. Hee hee.
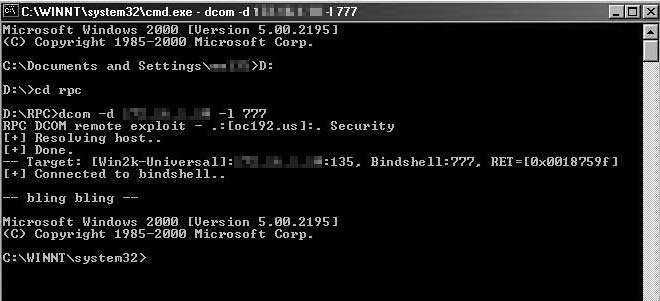
Then, in late October, we did some port scanning on the internal network. We found some interesting ports and a lot of "135s" on many of the computers at school. So, we searched for some RPC DCOM exploits and found a bunch on Google. I took one to school and tested it on one of the servers that had the most ports open, especially that one special port.
Bingo! It worked! We had command line access to the server.
Next, we uploaded PWDUMP onto the server and grabbed the password hashes. We mapped out what the network looked like and it was basically four main servers: one for grades, one for financial stuff, one for the website, and one for e-mail (which was the vulnerable server). We couldn't access the web server, because it used different passwords than the ones that we were able to obtain.
After we grabbed the hashes, we decrypted them using John the Ripper and LC4, but we hit another bump. We found out that the administrator password that we had cracked wasn't the right password for the library and computer lab computers, so we couldn't install anything on those computers. But, the Windows 2000 family shares root access to all its hard disk drives by default.
Meaning we could just "Map Network Drive" to the other Windows servers and then access the server with all the grades on it. Once inside, we found a copy of the program that they used to enter all of our grades and store every student's information. It was in a 3 GB folder and we downloaded the entire thing onto our external hard drive.
We were shocked to find that the program contained every student's address, phone number and social security number, as well as their parents' Social Security numbers. Since we had the entire faculty's passwords, it was easy to gain access to the information.
We were also able to download teachers' e-mails. One of the e-mails gave instructions on how to use the grading program and how to set it up correctly so that it would properly connect to the grade server. I found a copy of it on Google and was able to change my grades during lunch time in the library. We also found out that the school's website had a link to the school's grade server and that, if you added port 82 to the end of its URL: http://GradeServer.schoolname.com:82
It would direct you to a secret site where all you had to do to gain access to a teacher's grade book was type in their name and password.
In conclusion, one vulnerability can lead to another. That's the importance of updating your computer, especially if it's a server and especially if you're an administrator in charge of 400 computers as well as four servers that hold the personal information of over 2000 people.
All of the programs that were used to do everything described were available for free by searching Google.
Shout outs to: H.N., J.L., C.R., J.M., J.K., R.P., S & J, T2, The Easter Bunny, ot, hb, ed, gm, jesus, and santa.