How to Improve Zone Protection in Burglary Alarms
In this article, I present a novel design of a hard-wired zone control panel or zone expander input of a burglary alarm, which provides an enhanced security level against compromise attack attempts or problems with the zone loop.
Burglary alarm systems in question feature zone input connections with RF sensors and hard-wired sensors. Herein, I review the positive and negative properties of such zone inputs and the degree of susceptibility toward a variety of attacks compromising the secured zones.
A simplified schematic of a device for testing a sensor's hard-wired connections against compromising attack attempts is presented.
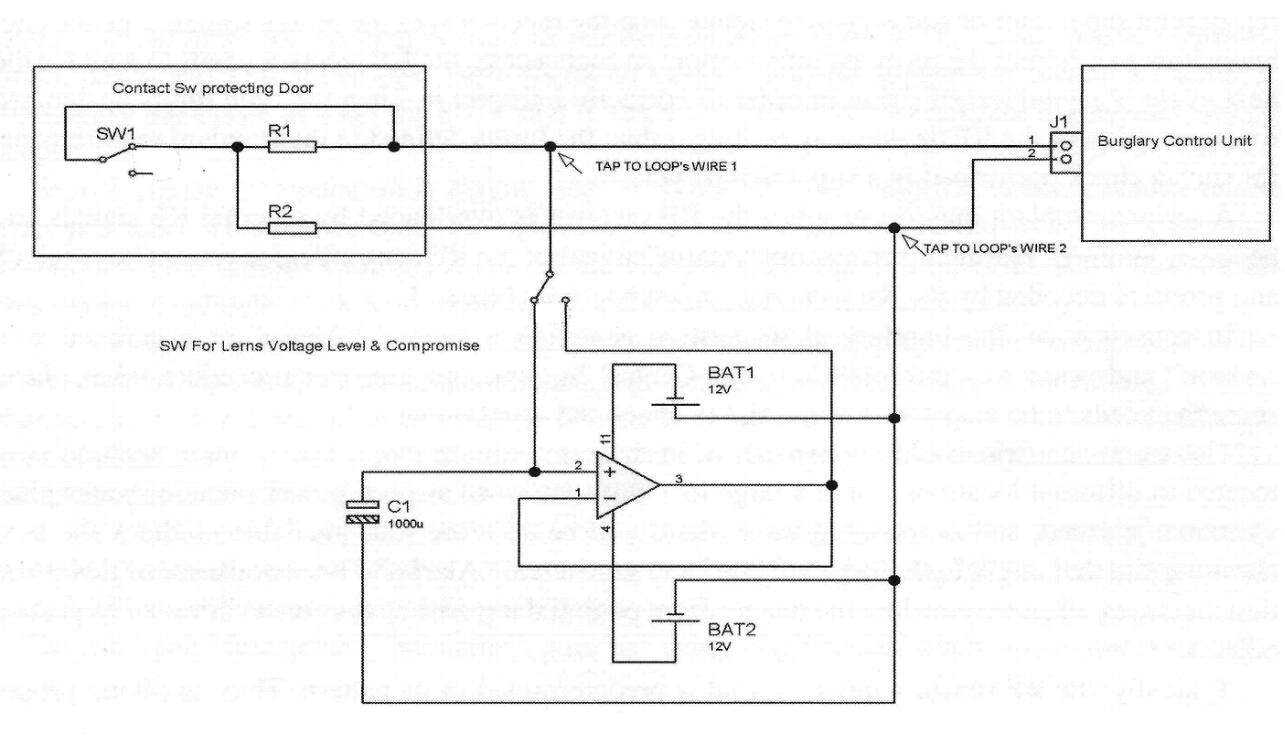
Figure 1: Simplified Device Used for Compromising a Hard-wired Zone Loop
Do modern designs of burglary alarm systems properly and reliably protect objects or zones?
This question will be answered by discussing a particular subsystem of a burglary alarm, the zone input, and its contact or switch that controls the status of a door, window, PIR (Passive Infrared Sensor), or other mechanical sensor barriers.
Modern Designs of Burglary Alarm Systems
Modern designs of the above sub-circuits provide two main technical solutions:
- The hard-wired zone inputs.
- RF (Radio Frequency) zone input.
Each of them has their advantages and weaknesses.
In the case of a hard-wired zone input, the contact or switch of the sensing device, usually combined with two resistors, is connected to the zone input of the burglary control unit or to the input of the zone expander of the burglary control unit. These zone input devices can be placed at a distance of several meters apart and thus may increase the installation costs.
The activation of a contact or a switch shorts or opens one of the serial resistors and thus changes the overall loop resistance. The changes in loop resistance will cause a burglary control panel's status to change from "Normal" to "Alarm" if the burglary system is armed, or to "Trouble" when the system is disarmed.
Additionally, abnormal events, such as when the zone loop wires between contact or switch and the zone input device become shorted or cut, will also generate an "Alarm" signal.
The greatest advantage of the hard-wired zone input type is that any changes of the zone loop resistance will generate adequate burglary alarm status immediately within the time limits described by the burglary alarm's system standard so that the hard-wired connections are constantly supervised.
However, a serious disadvantage of the hard-wired connection is that it is really easy to compromise or default the zone loop. This will be discussed below.
Compromise of the RF Type Zone Devices
The RF type zone input is an over the air type connection utilizing a sensor with a magnetic contact, or a switch like a PIR, or a door device with a built-in RF transmitter that sends its status to the RF zone receiver of the burglary control unit or the RF zone expander.
These types of connections generally are less expensive to install. However, these connections have some disadvantages.
The basic problem comes from the fact that the RF device has to periodically send a supervision signal within a maximum time frame of a few minutes, as defined in a particular standard. When a system uses several dozen RF devices, a situation may occur when two or more RF sensors concurrently send supervisor or status change signals, and the receiver sees the messy signals and does not know how to interpret the received information. In such a case, the RF receiver needs to wait for the next cycle of signal transmission in order to correctly interpret it. Then the time limits designated for supervision of the RF device may be longer than the limits defined in the standard requirements for such a check performed in a supervision cycle.
A serious problem may occur when the RF receiver is overloaded by external RF signals and becomes jammed. During this time, the "Alarm" signal of the RF sensor device cannot be received and properly decoded by the RF receiver - it just becomes blocked.
In consequence, the burglary alarm system generates a general "Alarm" or a jammed type "Alarm" and sends this information to the Central Station, and a proper procedure takes place: someone needs to be dispatched to the site to check the situation.
The worst scenario could happen when, in the same time frame, a few or more secured sites located in different locations - or at a large location such as an airport, power plant, or water plant - become jammed, and as a consequence, there will be no more staff available to check the next alarming site that might actually be attacked and send a real "Alarm." The seriousness of this situation increases when we consider the danger from potential terrorist attacks on a variety of important objects.
Typically, the RF sensor's device signal is predetermined in its pattern. Thus, applying proper RF devices and sniffing/spoofing techniques, a false substituting signal can sent with a status of "OK" right after the original RF sensor is physically destroyed. However, these compromising techniques require access to proper RF equipment and people with adequate knowledge and experience.
All of the above problems are consequences of the fact that the RF signal may be visible to anybody with appropriate devices.
Compromising Hard-Wired Connections
Considering all of the above, hard-wired type connections seem more reliable and safe in securing a wide variety of sites. However, in order to make a hardware type connection safe, we need to solve the problem of compromising it.
Because the hardware zone loop is powered by a constant voltage level delivered by the burglary control unit or a zone expander, it is very easy to apply devices that can read and remember the voltage level in the zone loop and later, on a request, feed it back to the zone loop.
When, for example, the applied compromising voltage level represents the status of "closed door" (window or other barrier), then opening the door (window or other barrier), will not affect the zone loop voltage level because a burglary control unit sees the zone loop status as not changed. In this way, someone can access a protected area without being noticed.
Figure 1 shows a simplified example of compromised devices and tactics, and a way of taping it to the zone loop wires. These types of devices allow compromising the protected zone loop for a time frame of up to 30 minutes or even longer.
To be more precise, based on Thévenin's theorem, if an external compromising voltage equals the voltage level presented when the door is closed, and if during the compromise attack this voltage is applied to the zone loop, then opening the switch or contact that usually changes the serial zone loop resistance will have no effect on the loop parameters seen from the zone loop input terminal, as the compromising voltage compensates for the loop resistance changes.
In the case where more than two wires count in a zone loop, more compromising devices may be used to connect to the wires in a circular pattern, in order to monitor and then substitute all voltages presented in the zone loop circuits.
How to Prevent Compromise Attacks on a Hard-Wired Zone Loop
The case presented above is of such importance that it needs to be prevented. This can be accomplished by changing the way the zone loop is powered, from DC with a constant voltage level to a random variable voltage level constantly changing over time.
As the results of applying a random variable voltage power to the wired zone loop, as shown in Figure 2, it will be extremely difficult to successfully perform any of the above discussed compromise techniques in order to disable the protected zone.
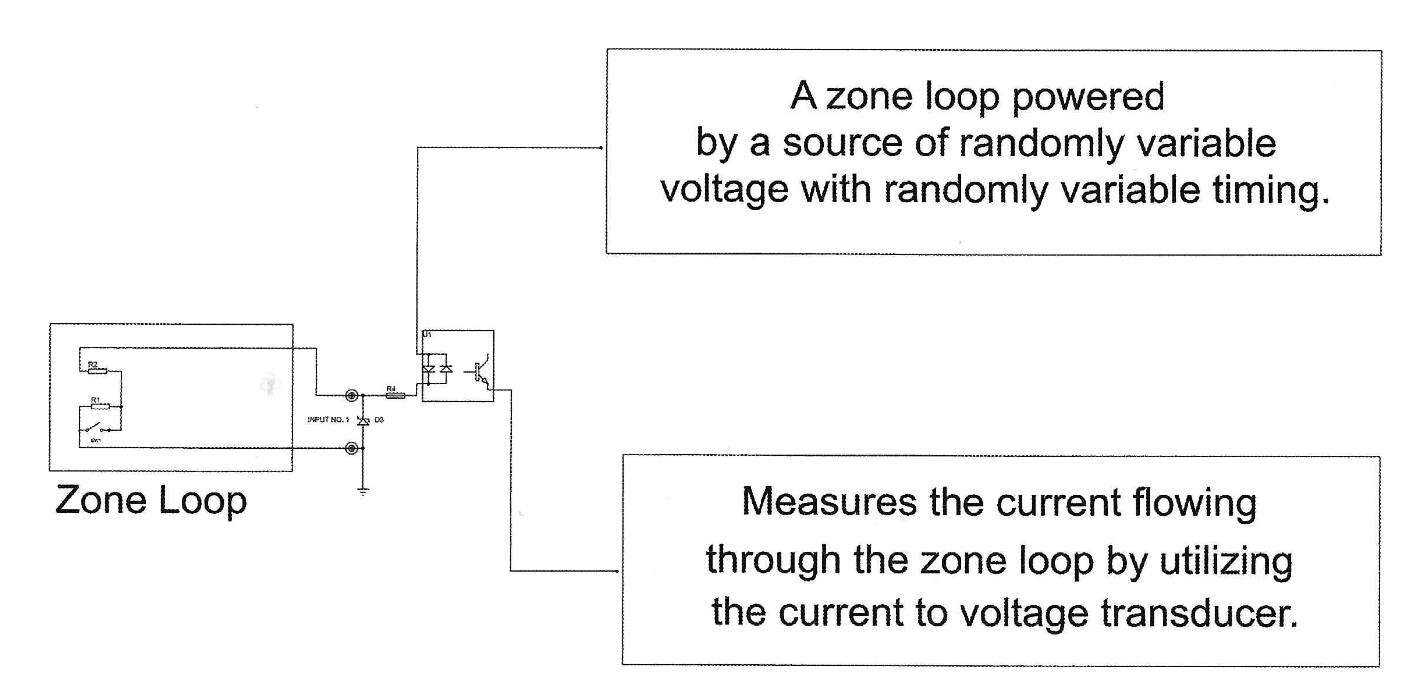
Figure 2: A Wired Zone Loop Powered by Random Variable Voltage and Timing
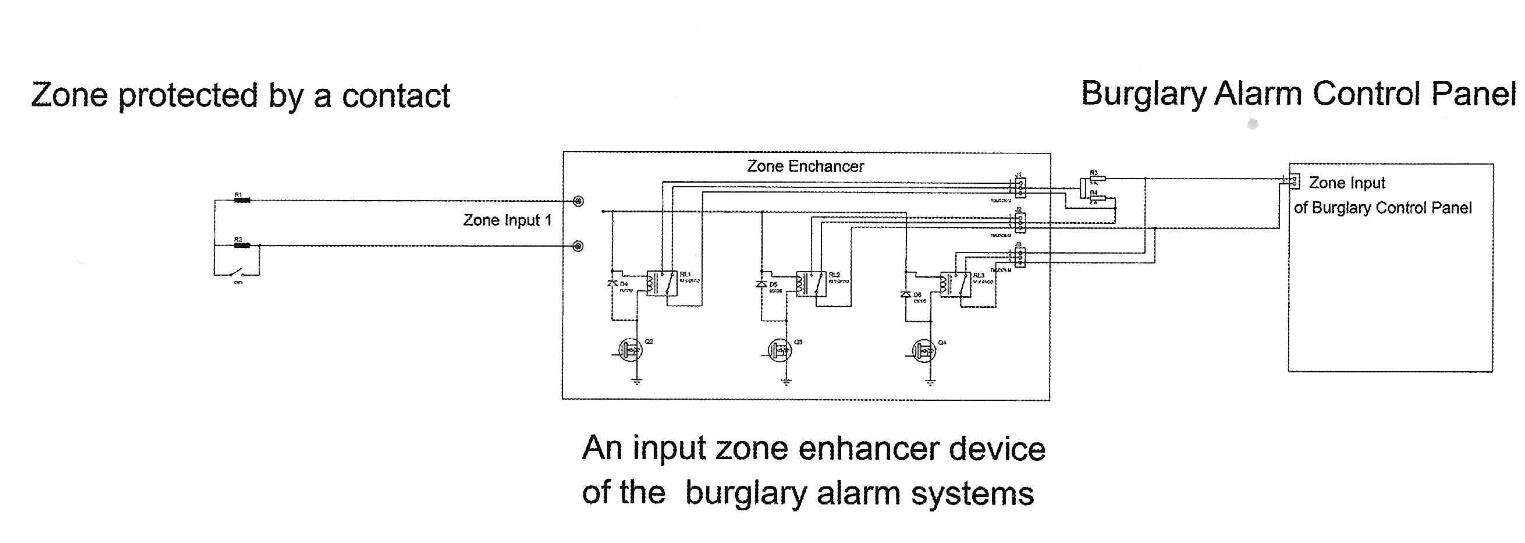
In practice, the easiest way to protect a hard-wired zone loop would be to insert - between the zone loop and the burglary control panel - a device called a Burglary Alarm Zone Enhancer, which will power the zone loop with random variable voltage level and will process the status changes of the contact or switch and pass the result to the input of the control unit as shown in Figure 3.
The device named Burglary Alarm Zone Enhancer described above has a patent pending status. If you are interested in this subject, feel free to contact me.