Now, while we´re here in winice.dat we can also modify the init-string for softice (you can add some initial settings here that are executed on every start of softice). The init string i use is INIT="wl;wr;ww 3;wd 3;wc8;watch eax;watch ds:si;watch es:di;" which sets watch-windows (they display the content of the given location permanently so you dont have to display them all the time with the "d
The installation of softice has added a line in your autoexec.bat file like C:\SI95\WINICE.EXE which loads softice into the background before windows is booted. It will rest there invisibly, until you press the key-sequence to pop up the debugging screen. The usual key sequence to bring up the softice-screen is ctrl+D (this can also be changed with the appropriate command in the INIT-String). If you only get garbage (hey ! asm-code and hex-values are NO GARBAGE !) after this, say like strange coloured keys, a system-crash, blank screen etc..., you might have (99% chance) a problem with your video-card and the s-ice display adapters. Refer to the Getting Started - Section at the top of this page to find a solution to this problem. If you are lucky enough that you get a proper screen, it should look like this:
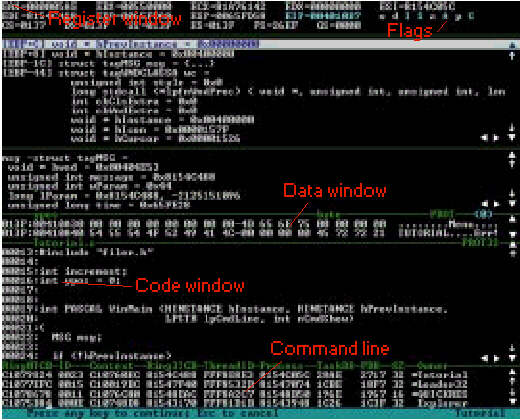
The screen on the picture is *slightly* different from the one you will get, coz you wont have the window-section between the Registers and the Data Window. This is due to the fact that you wont have any source code for the programs that you reverse engineer (it wouldnt be very wise to ask "why?" at this point...), so forget about it, okay ? Now to the marked windows... Everyone with a slice of ASM-knowledge knows what the registers are, so the register window is where the current values of them are shown. You can toggle this window on/off with the "wr" command. At the right hand of the Register window are shown the current states of the flags (the Zero-Flag is the most important one for our tasks, coz the execution of the conditional jumps jz, jnz etc. depend on it), if a flag is set its corresponding letter (eg. Z for the Zero-Flag) is highlighted. The data window displays data in memory, it is toggled with the "wd" command (if you want to display more lines for the data window you can set it to the desired state with "wd (number-of-lines)", use the same syntax for the other window commands... when adjusting one window you might have to adjust the other windows after that as well, so start setting the line-numbers for the top window and then go down respectively - otherwise you might mess up the other windows if you start configuring e.g. the code window first ;-)). You can display a specific memory location with the "d (location)" command, where location is the address in memory you want to examine. Underneath is the Code window, where the currently executing code part (in ASM of courze ;-)) is displayed. The highlited line shows the command which will be executed next. You can toggle this window with the "wc" command, "code on/off" changes the display of the opcode for the asm-commands. I guess that there is no need to explain the Command line, you simply type your softice commands here.
Now, i explained above that you need to set breakpoints on certain events in order to get to the desired code parts of the debugged program. There are a few commands in order to make work with these breakpoints a bit easier. First thing is to list all your current breakpoints you have set, you can do this with the "bl *" command. S-Ice then lists you the breakpoints in the order of setting (each Breakpoint has a number assigned to it by softice at the time of setting it, so the first breakpoint you set gets number 0, next one 1 etc...). When a breakpoint isnt of importance anymore after you breaked on it for the first time, you can disable it. Lets say for instance you breaked on hmemcpy (used for copying strings in memory) in order to find a serial-number check. After you found the code part with the serial-check, you might not want to get disturbed in your stepping thru the code by other uses of hmemcpy because you want to step over other string routines and focus on the compare at the end of the check (or maybe on the martini, who knows ?). Then it would be wise to disable the breakpoint on hmemcpy with the command "bd (number-of-breakpoint)". You can disable ALL active breakpoints with "bd *". To enable the breakpoint again, use "be (number-of-breakpoint)" or respectively "be *" for all of them. If you want to remove a breakpoint completely from the list (no matter if its enabled or disabled) you can do that with the "bc (number-of-breakpoint)" command or "bc *" to clear the whole list. These commands come in handy when checking for several different occurences, its a nice feature so use it !
The thing you will do most of the time when debugging a program will be the stepping thru the code. The highlighted line in your code-window marks the next line of code that WILL BE EXECUTED (so its not executed yet !). In order to single-step (that means to excute the next single line of code) you use the "t"
command. If the next line of code is a call, you can SKIP the stepping INTO the routine by pressing "p" which steps over the call (its executed as well, you just dont step INTO the subroutine) and stops at the next line after the call. You will need "p" or F10 quite often, coz you will find a lot of uninteresting windows and system-calls you want to step over.
In case you step into a routine you want to get out of (meaning returning to the code-part that called this sub-routine) you simply press F12. Thats easy, isnt it ?