 Mark Abene
Mark Abene
interviewed November, 1993
When people ask you what you do for a living, what do you say? Well, I usually tell them I work for Echo... Before that, either that I was unemployed, or just a freelance, hacker-type person. How old are you? 21. When did you first get into computers? Probably when I was about 10 or 11.... The first computers I used were at the local shopping mall. I used to play a lot with a Texas Instruments TI-994A. This was when the whole idea of PCs was fairly new. So, I played with those, I played with Apple IIs, I played a little with VIC-20s at the time...It was kind of fun, programming in BASIC... printing stuff on the screen, getting input from the keyboard. And you taught yourself programming. Yeah, the first thing I did, I taught myself BASIC.... It was fun, for a bit. I liked to play video games.... Before I got into computers, I had an Atari 2600. I played video games a lot, in the arcade too... It was the pre-Pac Man years. Elevator Action was a favorite of mine, Jungle Hunt was another one. What was the first computer that you ever bought? I was gonna get a Texas Instruments computer; it was around the holidays. But I ended up getting a Radio Shack computer... a micro-color computer, which has since been discontinued. I was really great. When I first got it, I had a whopping 4K of memory, and it was hooked up to my TV. And I would just type stuff in, [programs] from books.... I didn't have any means of saving, so either I would just leave my computer on and shut the TV off... Sometimes I typed in some really, really long programs, that I didn't have to want to type in over again.... It wasn't too long before I got a cassetterecorder... and I got some software on tape. Actually before [that], I got the memory expansion, so I was just kickin' ass with 20K of memory... When did you get your first modem? I got a modem, I think a year or so after that... and I was really excited about it. I didn't know exactly what to expect, but I knew, like, I could call stuff, I didn't know what, either... When I got a modem, it's like, 300 baud was the modem. 1200 bps at that time was exotic.... And I remember I got my little starter kit for Compuserve, that came with my cassette software. You take it for granted now that we have these big PCs, I mean, even 80 columns -- I had 32 columns on my computer, and with no lower case! So doing stuff online was a challenge. How'd you like Compuserve? Compuserve was great, at first, because I was able to contact people. And I was trying to find people that had the same computer as me, and I found a couple, but not very many. I was only on Compuserve for, like, a couple of months before I ran up an outrageous bill, and, obviously, I stopped calling it. Before that, I'd gotten numbers of BBS's from people. Originally, they were just BBS's for just TRS-80 computers, for, like, software and stuff... Through people that I'd met with the same computer, I found out about, like, other sorts of BBS's, that didn't necessarily pertain to software and stuff, but like, hacking-type stuff. It was strange, because at the time, we had never had a need for a touch-tone phone, and I don't think it was very often that I used a touch-tone phone. We just had a rotary phone. In fact, in my kitchen, we still have a rotary phone. And this was before the days of smart modems. Smart modems were fairly new -- modems that could dial on their own. In fact, direct-connect modems were fairly new. I had a 300 baud direct-connect modem, that you could plug straight into a phone jack in the wall. Because at the time, not very many people had phone jacks. We didn't -- I had to actually get the little phone jack kit from Radio Shack.... So, calling these BBS's, you first learned about hacking. Yeah. My first brush with it was, um -- some BBS's that were computer and software-related, a couple of them had these little sub-sections, that might have been related to hacking. Now it's really frowned-upon, but at the time, in the early 80s, it was very, very commonplace to collect and trade calling card numbers. And it was just normal. No one thought twice about it, because they were just so much in abundance...They were ever present, and they were relatively easy to get... it was a common thing. I mean, now I'd frown upon something like that, but, back then I didn't know much about it, and it just seemed like the thing that everyone was doing. And I'm not saying, "Oh, since everyone is doing it, is it okay?" It was never even thought about. I was like 13 or 14 years old, and it was just the thing people did. And in fact, when I first came across them, I couldn't use them, because I didn't have a touch-tone phone! Tell me about the infamous "Legion of Doom." My first brush with the "infamous Legion of Doom" was -- At the time, there was a very large concentration of BBS's in Long Island, in 516 [area code]. Not so much in 718 or 212, for whatever reason. As far as the closest thing to local, like within New York, there were a lot in 516. And, I remember, there was a BBS in Long Island that was sort of Legion of Doom-affiliated. And you would just call it up and connect, and it would say "Password." And we didn't know what to type, and it just hung us up. So I was like, "That's pretty interesting. I wonder what it is?" And apparently it was some members-only, Legion of Doom-affiliated BBS. So I wanted to find out more about this stuff, like just what these people did in general. Around the same time period I saw War Games -- that came out around that time. A lot of things coincided around the same time, like me wanting to find out more about this stuff, and computers in general. Some of the first systems that I logged into, that, you know, weren't mine -- I wouldn't go so far as to say didn't have permission to -- they were guest accounts on a couple of universities on Long Island... they had a bunch of DEC minicomputers. They were PDP-11 machines, and they were running an operating system called RSTS... it was a multi-user time-sharing system. And I logged into a couple of these on guest accounts that were just open for anyone to use. I remember the feeling I got from trying out these big minicomputers...the fact that I could use my computer -- I mean, it's kind of silly to think about now, but at the time, thinking that I could use my computer to connect to another computer that was more powerful, and use it as if it was mine -- I'm telling it what to do with my keyboard, and it's giving me responses on my screen. I'm like, "Well my computer's so small and limited, but I can tie into this bigger, powerful computer with all sorts of people on it, and all sorts of programming languages, and disk space and stuff.... The idea that I could write a BASIC program on this minicomputer, and save it, and then log off, and wake up the next day and log in, and my stuff is there, you know, in this guest account -- stuff that I created... you know, it gave me a sense of -- the fact that I had these utilities at my grasp, to takeme further in "the mission" to learn new things... So, you wanted to do more... Yeah, I wanted to find out more about these bigger and better machines. If you saw the computer that I had then -- it was a little tiny thing, and it was extremely limited, and I pretty much took it to the extreme of what it was capable of doing. In fact, I remember writing a letter to Tandy, in Texas, wanting to know more about machine language, and hi-res graphics and stuff like that. And I got a phone call from someone at Tandy, saying, "Well, we didn't think anyone would ever do those sorts of things with that computer. It was just supposed to be, like, a toy computer. We didn't think anyone would be interested in it, to take it further." So I had nowhere to go from there, as far as support for my computer. I hooked up with a user group, but, again, that can only take you so far. And I was interested in technology in general. Sometimes I think about a memory that I have, of when I was about three years old. I had gone to visit my sister, with my parents, at SUNY Albany -- she was a student. And they were having -- apparently just from this faint memory I have -- they must have been having some sort of computer fair or something... I remember seeing all sorts of weird things, like robots, and, these big mainframe computers. And I'm sure I didn't know what a computer was when I was three years old. But just seeing all this stuff -- it was a big curiosity. That was probably the seed that was implanted in my memory, that was sort of in the back of my mind, until it was awoken years later... Well, as far as lore goes, in the early 1980s... teenagers who called BBS's that were supposedly part of the so-called "hacker scene" or the "phreak scene" -- there's a lot of posturing that goes on, sort of one-upmanship. And people would form little affiliations and groups and stuff, just at the drop of a hat. It really had no meaning. In fact at the time, the Legion was just another one of those type of groups that was trying to make a name for itself... It was just a group of people who were somewhat anonymous to eachother -- at that time period, no one knew anyone in person, no one ever met anyone face-to-face. In fact, no one knew anyone's real name, and a lot of the time, no one knew even where they were from -- what state they were in. It was completely anonymous. And people went to great pains to maintain their anonymity. It was considered really a distressing thing if someone found out who you were, and what your personal information was, because it was something that was closely guarded. People were extremely paranoid about things like that, because they were doing what would probably be termed as "subversive" things... So what sorts of things did you do with the LoD and MoD? I had met people who were affiliated with the Legion a couple of years later, and I remember, a friend of mine in Florida, who I'll leave nameless, because, like, he must be like 30-something years old today, and he has a professional life -- he was one of the first people I had "met." We usually use the term "met" loosely, and it usually means "above the anonymity phase" -- like if you've gone so far as to talk to the person on the phone, then you might consider that as having "met" the person. Because just running into them on a BBS didn't go so far. And, again, a BBS was something as simple as a little 8-bit computer on some kid's desk in his room, with a couple of floppy drives. If he was really lucky, and his parents were really nice to him, they might have gotten him a hard drive, but it was usually just a kid with a little 300 baud auto-answer modem, and a couple of disk drives. One phone line -- if it was busy, it was busy, you had to wait. And that's how they all were. It was very rare to find a BBS that had more than one phone line.... LoD was probably more organized than a lot of them... Legion of Doom is something that seemed to persevere as time passed by... It was more or less sort of an effort, by certain members of this loosely-knit group of people, who, you know, would run into eachother on certain BBS's. They wanted to find people, and get them in contact with eachother, to more or less "network" people, you would call it today, and sort of have "meetings of the mind," to spread the learning process. Everyone was more or less interested in learning more about powerful machines, and how they worked, stuff like that... And how to get into them... Getting into them wasn't really the thing, it was something that was related. Obviously, in order to play with the machines, you have to get into them. But the main focus wasn't to get in; the main focus was what to do once you were on. But of course, you have to, in order to know how to get into a machine and maintain your access to the machine so you could learn about it, you know, it was necessary to learn stuff about security, and stuff like that.... At what time did you realize you might be breaking laws? Well, at the time, it wasn't illegal. It simply wasn't. I mean, it was a rare case when you found out about someone was prosecuted under some law that was made to fit. But there were really no clear-cut laws specifically pertaining to computer trespass. Was there any warning that you might be busted, or was it a total surprise? Well, the first time it happened, things were different. People were getting into trouble at an alarming rate. Prior to that, it happened very rarely. I mean, you might read about something in the paper, but it was pretty rare, and a lot of it was just badly written propaganda, like by some writer for some newspaper that just didn't get it... The first time you were busted, did they knock on your door...? I wasn't home, the first time. It was in the evening, and the Secret Service had come, and somebody was home. So they pretty much just hung around until I got home in the evening. I was working at the time.... They pretty much took all my stuff, and I've still never seen any of it. Compared to that, when they came back, the following year, it was a lot more violent. It was like 11 in the morning, and they had broken into the house, and I was the only one home. It was the FBI and the Secret Service. I was asleep, and they just pulled guns on me and woke me up. And they pretty much just rummaged through the whole house. What were the charges? The charges were, um -- see, this is what's odd. They don't have charges, they have suspicions. They come up with the charges later... It's like they shoot first and ask questions later. They suspect something, usually just based on really shabby sources. Then they write a really convincingaffidavit for a judge to sign -- a warrant. I'm sure they had to say some pretty hairy things, because they got the judge to sign a "no-knock" searchwarrant, which means they could just break in.... It was December of '91, and it wasn't until the Summer of '92 that they put together like a20-something-count indictment, or even more than that... It was involving five people, and only two of the accounts really involved me, out of all of them. Two people were a main focus of it. I was more or less like, "He must have been involved" kind of deal. You know, "He's probably involved, he's talking to these two guys. I'm sure we'll find something, if we raid his house." That's pretty much how they went about business. You pleaded Not Guilty. Originally, yeah. I entered a Not Guilty plea, because I had gone through something similar the first time, although I was underage -- I was justcharged as a youthful offender, and nothing ever became of it. It was a misdemeanor, it was a state thing, because I was a minor, and all that.... I didsome community service for the first time. And it was pretty much over and done with, until later that year... I never really got the impression that things were over and done with. I'm sure it was lack of planning on their part that they couldn't charge me as an adult, because at the time I would have been 18 only about a month later. So I'm sure things were festering for quite a bit. And obviously the investigation never closed. There was still an investigation on-going throughout the whole time. So, the second time, it was a felony. Yeah, I eventually ended up pleading guilty to two felony counts... conspiracy, which was, basically -- the conspiracy charge in the indictment described a couple dozen what they called "overt acts," which, for the most part, didn't involve me. But since the count partially involves you, it's still the same count. So it's as if you're pleading guilty to the whole thing. And the second count was "unauthorized access to federal-interest computers." That's really non-specific. All the laws they came out with, or that they revised in the mid-80s, to make them a lot more, what they thought were, specific, are really blanket laws, that are really non-specific. And they try to include as many things as they can. In fact, when you read the search warrant for the things they're allowed to seize, it's pretty much like, you might as well say, "Anything that isn't tied down." But they try to make it sound like "anything electronic." You dialed up phone company computers, and... Yeah. I was, still am, interested in telecommunications engineering, and the science of it too. Being able to actually access and learn from the actual machines themselves in the infrastructure -- the real equipment, you know, as it is, in the field, is very educational, in my opinion.... It goes a lot further than taking a course or reading a book -- actually utilizing the equipment, and seeing it in practice... What were the government computers? That's pretty much them. I mean, when they say "federal-interest," I guess they mean anything that the government has a vested interest in -- anything that's infrastructure, anything that sounds important... How about TRW? TRW is more involving some of the other people that were charged in more of the counts. And TRW -- not as far as government contracting,but, their branch of credit reporting. Some of the counts in the indictment involved credit card fraud. And I wasn't charged with any of those things --they didn't involve me. There's this famous incident where you downloaded John Perry Barlow's credit onto the Well... Oh, yeah. At the time, I was about 17. There was a forum that Harper's magazine was holding on tThe Well in Sausalito. And i was invited through a friend of mine, Emmanuel from 2600 magazine. Me and a friend of mine [Paul "Acid Phreak" Stira] were invited to take part in this forum. It was only supposed to last, I forget, like a month or a few weeks or whatever it was. And a lot of the people in the discussons were very non-receptive of me and my friend, and Emmanuel. For whatever reason -- I mean, I'm not totally sure myself what the reasons were, but there was a lot of prejudice going on between the older, West Coast mentality of, you know -- you still hear it today -- the whole "hacker/cracker" nonsense that has sort of plagued the Net. And it's just a lot of noise, and a lot of wasted bandwidth -- just petty bickering going back and forth, about, you know, who's purer than the other guy... The reference I always use... there have been books written, like The Hacker Crackdown, and other stuff like that. In my opinion, in general, is that they pretty much suck, as far as the method that the author told the story -- it was pretty much from the author's perspective, which was fine, but I never read anything that hit the mark. The only book I ever read, which I read at a time, you know, I was developing ideas, and what my ethics were, of what I was doing -- what I thought was right and wrong -- it was when I read the book Hackers by Steven Levy...which is the only book that I know of that ever portrayed anything in a respectable light. And it was before the whole "hacker/cracker" nonsense. It told the story -- all the legends and lore, from the very beginning, from, like, the 50s, until today, of the guys who were the pioneers of this stuff -- hacking, at MIT, and UCB, and Dartmouth, and those colleges. What's the difference between a "hacker" and a "cracker"? I don't use the word "cracker," so I don't draw any difference...The only difference is that I don't use the word, and I try not to pay muchattention to people that do. How do you define "hacking?" I don't have any problem with the way that Steven Levy -- after he met and talked with all the people, and the conclusions that he came to -- I prettymuch agree with it. And it's that hacking is striving to learn as much as you can about something, and using it for, you know, towards positive goals, or for a greater good... And that there's no such thing as forbidden knowledge, or copyrighted information; that knowledge is for everyone to learn, and grow from, and better themselves with. Phreaking originally had separate roots from hacking, but they sort of converged, and now you don't really hear about the term "phreak" beingused all too often anymore, because [they're] pretty much one and the same, as far as the involvement of people. At the time, phreaking, like in the 60s, had to do heavily with -- it has its roots in "blueboxing." Blueboxing -- it sort of came about from people who had read some Bell system technical journals, which isn't secret knowledge or anything. It's a technical journal that you can find at most universities even today; it's very good reading. And at the time one article was published by an engineer at Bell Labs about the frequencies used -- they're actual audible tones used in trunk signalling, between switching systems in the telephone network...the way that switching systems would signal to eachother to place calls and to route calls, and so on and so forth -- operator functions, and things like that. So now that you've gone through all this legal stuff and you've pleaded guilty, are you sorry? Well, I'm more sorry that the world is such that people literally have to break laws in order to want to learn more about things.... There isn't a better medium through which to gain access to this sort of information, to learn from it. And that there's no other options that you have at your disposal, if you're interested in these sorts of subjects...I think it's just unfortunate that that's the case, and, little has changed in that respect. All of the other people in the case have already been sentenced... Except for one person, who was going to testify against me, who turned into an informant, who will probably be sentenced after me. But out of the five people, three of them have already been sentenced, and they're already serving their sentences. Did they get jail time? Yeah. One of them got a year and a day, and he's doing half of that in what's called a "shock program," which resembles a Marine boot camp for "hardened kids." He's not a "hardened kid," and the only reason he went into the program was because he was able to do half the time. The other two people got six months, and six months in, I think, home detention after that. And then three years probation and 1000 hours community service. What do you think you're going to get? Hopefully I won't do worse than that. All I can do is hope that I can do better than that. It's very distressing having to worry about something like that. Suppose you go to prison and serve six months or something. What are your plans for afterwards? I don't think that -- and I'm going to be as honest as possible -- I don't think I'm in the frame of mind right now to think about that, because I've just grown so accustomed to the stress and the anxiety of a pretty bad situation that's just been around for a pretty long time. It's been a very limiting factor in my life, and what I want to do with it, over the past few years that it's been going on. It's been going on a very long time. And when it's resolved I think I'll have to start rebuilding and picking up the pieces. Before we finish, tell me what your favorite pieces of computer hardware and software are? Let's see. As far as favorite software, if it's not Unix, I don't like it. As far as computers themselves, uh, if it's running Unix, it's a step in the right direction!... Because I like Unix; because I think it's the best thing since sliced bread. What about the new technologies that you coming, that you like? Well, a lot of this stuff could be referred to as "vaporware" right now. There's a lot of things and ideas that people are coming up with, and I don't think people know where it's going. But you're seeing corporations are trying to have a convergence of technologies. Like phone companies signing deals with cable companies, and things like that. Because they want to "bring newer and better services to the home"... Considering that the average person has trouble programming their VCR -- this is the example everyone uses. They've got to resolve these things. I mean, sure, it's going to be great if I ever get my hands on the technology. But they're not marketing it toward, like, a few whiz kids, or a few rich corporations. They want to market things on a grander scale... And I'm sure it will be interesting in the next decade to see all the new services that become available. You've been all over the Internet. What are some good places to visit? Oh, I don't know. Well, Echo is certainly a cool place to hang out on the Net. In fact I'm there quite often! [laughs]. But I don't know. I mean, it's kind of surprising the way things have changed, the fact that Internet has become such a public place. Because, when I was first getting into things, Internet wasn't really known too much as Internet -- it was known more as ARPAnet... It was more or less not too well known outside the scope of universities and research installations and stuff like that, because that's the main reason it came into being. So early on I wasn't really involved too much with the Internet at all, but now that it's become a lot more public, it seems to be where it's at. But I wouldn't say there's any one specific place that I favor more than any other place on the Net. I just like the fact that something like it exists as a whole...I think it's very beneficial to the growth of society, to hopefully bring people closer together. Mark Abene's story is chronicled in Masters of Deception: The Gang That Ruled Cyberspace by Michelle Slatella and Josh Quittner. (HarperCollins, 1995.)
 How did you get involved with people like the Legion of Doom?
How did you get involved with people like the Legion of Doom? 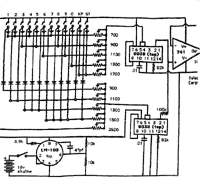 What about "phone phreaking." What is that?
What about "phone phreaking." What is that?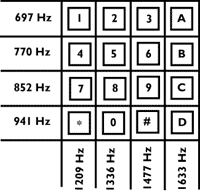 It was only a matter of time before electronics hackers and hobbyists designed little circuits to play with, that mimicked these tones. [They] experimented, and were able to, basically, signal phone company trunk lines with these tones, and explore the telephone network on a grand scale. Basically by listening -- it was hacking, but there was no visual aspect to it. It was completely something that was auditory. It was like, you signalled some tones, and you listened for what you got connected to... it's sort of like touch tones -- this pair of tones indicate the number one or the number two -- it's along the same lines. So you have a set of tones, basically zero through nine and a couple of control tones. And you could signal to other trunk lines, you could place telephone calls, you could reach things that aren't directly dialable with a normal telephone.
It was only a matter of time before electronics hackers and hobbyists designed little circuits to play with, that mimicked these tones. [They] experimented, and were able to, basically, signal phone company trunk lines with these tones, and explore the telephone network on a grand scale. Basically by listening -- it was hacking, but there was no visual aspect to it. It was completely something that was auditory. It was like, you signalled some tones, and you listened for what you got connected to... it's sort of like touch tones -- this pair of tones indicate the number one or the number two -- it's along the same lines. So you have a set of tones, basically zero through nine and a couple of control tones. And you could signal to other trunk lines, you could place telephone calls, you could reach things that aren't directly dialable with a normal telephone.