|
Contents:
Web Bug FAQ
Bugnosis General FAQ
Bugnosis 1.3 FAQ
Bugnosis 1.1 FAQ
 Web Bug FAQ Web Bug FAQ
What exactly is a Web Bug?
A Web bug is a graphic on a Web page or in an e-mail message designed to monitor who is reading the page or message. Web bugs are often invisible because they are typically only 1-by-1 pixels in size. In many cases, Web bugs are placed on Web pages by third parties interested in collecting data about visitors to those pages.
What information is sent to a server by a Web bug?
 The IP address of the computer that fetched the Web bug The IP address of the computer that fetched the Web bug
 The URL of the page that the Web bug is located on The URL of the page that the Web bug is located on
 The URL of the Web bug image, which contains the information to be communicated between the Web page visited and the site collecting the data The URL of the Web bug image, which contains the information to be communicated between the Web page visited and the site collecting the data
 The time the Web bug was viewed The time the Web bug was viewed
 The type of browser that fetched the Web bug image The type of browser that fetched the Web bug image
 A previously set cookie value A previously set cookie value
(Although this might not seem like much, these items can be used to spread information between multiple Web sites. Click here for a more detailed explanation.)
What are some of the uses of a Web bug on a Web page?
Web bugs can be used to provide an independent accounting of how many people have visited a particular Web site. Web bugs are also used to gather statistics about Web browser use at different sites on the Internet.
In addition, advertising networks can use Web bugs to collect information on what sites a person is visiting to create a personal profile. The personal profile is stored in a database server belonging to the ad network and identified by the browser cookie of the network. The profile determines what banner ad one is shown at a later time.
A more detailed outline of the uses of Web bugs appears under Advanced Topics.
Why are they called Web bugs?
A "bug" is a small eavesdropping device. It's not a euphemism for a programming error.
Rather than the term "Web bugs," the Internet advertising community prefers the more sanitized term "clear GIFs." Web bugs are also known as "1-by-1 GIFs," "invisible GIFs." and "beacon GIFs."
Are all invisible GIF images Web bugs?
No. Invisible GIF files are also used for alignment purposes on Web pages. A Web bug will typically be loaded from a different Web server than the rest of the page, so they are easy to distinguish from alignment GIF files.
Are Web bugs always invisible on a page?
Yes, according to our definition. But Web bugs are not the only types of Web elements that can track user activity. See the Advanced Topics below.
How can I manually locate a Web bug on a page?
Before Bugnosis, the only way to find a Web bug was by viewing the HTML source code of a Web page and searching for IMG tags that match up with cookies stored on the user's computer. A Web bug will typically have its HEIGHT and WIDTH parameters in the IMG tag set to 1, it will be loaded from a different server than the rest of the Web page, and it will have an associated cookie.
I was visiting www.buy.com when Bugnosis told me about a Web bug from ad.doubleclick.net. Which company is responsible for the Web bug: Buy.com or Doubleclick.net?
The companies may have decided together to place the Web bug on Buy.com’s page. In fact, both Web sites need to add a little bit to their Web servers to put the Web bugs there. However, sometimes the main site — the one you are aware of visiting — defers such matters to the site actually providing the bug.
Why are they bugging me?
Companies use Web bugs to:
 Count the number of times a particular Web page has been viewed. Count the number of times a particular Web page has been viewed.
 Track the Web pages a visitor views within a Web site. Track the Web pages a visitor views within a Web site.
 Track what Web pages an individual visits across many different Web sites. Track what Web pages an individual visits across many different Web sites.
 Count the number of times a banner ad has appeared. Count the number of times a banner ad has appeared.
 Measure the effectiveness of a banner ad campaign by matching visits to a Web site to where banner ads for the site were originally viewed. Measure the effectiveness of a banner ad campaign by matching visits to a Web site to where banner ads for the site were originally viewed.
 Match a purchase to a banner ad that a person viewed before making the purchase. The Web site that displayed the banner ad is typically given a percentage of the sale. Match a purchase to a banner ad that a person viewed before making the purchase. The Web site that displayed the banner ad is typically given a percentage of the sale.
 Allow a third party to provide server logging to a Web site that cannot perform this function. Allow a third party to provide server logging to a Web site that cannot perform this function.
 Record and report the type and configuration of the Internet browser used by a visitor to a Web site. This information is typically used in aggregate form to determine what kind of content can be put on a Web site to be viewed by most visitors. Record and report the type and configuration of the Internet browser used by a visitor to a Web site. This information is typically used in aggregate form to determine what kind of content can be put on a Web site to be viewed by most visitors.
 Record and report search strings from a search engine to an Internet marketing company. The search strings are typically used to profile users. Record and report search strings from a search engine to an Internet marketing company. The search strings are typically used to profile users.
 Transfer previously input demographic data (gender, age, zip code, etc.) about visitors of a Web site to an Internet marketing company. This information is typically used for online profiling purposes. Transfer previously input demographic data (gender, age, zip code, etc.) about visitors of a Web site to an Internet marketing company. This information is typically used for online profiling purposes.
 Transfer previously input personally identifiable information (name, address, phone number, e-mail address, etc.) about visitors of a Web site to an Internet marketing company. This information is typically used for online profiling purposes. It also can be combined with other offline demographic data such as household income, number of family members, type(s) of car(s) owned, mortgage balance, etc. Transfer previously input personally identifiable information (name, address, phone number, e-mail address, etc.) about visitors of a Web site to an Internet marketing company. This information is typically used for online profiling purposes. It also can be combined with other offline demographic data such as household income, number of family members, type(s) of car(s) owned, mortgage balance, etc.
 Cookie sync, which allows two companies to exchange data in the background about Web site visitors. This data can be demographics or personally identifiable data, typically used for online profiling purposes. Cookie sync, which allows two companies to exchange data in the background about Web site visitors. This data can be demographics or personally identifiable data, typically used for online profiling purposes.
How many computers are involved when a Web bug is used?
Usually three. For example, suppose Alice surfs to Spend.com, which contains a Web bug. Technically speaking, the Web bug looks like an image embedded in the Spend.com Web page. In response to loading the Spend.com Web page, Alice's computer automatically tries to fetch the embedded image. But it was deposited in Spend.com in a way that says "the image is actually located at Bug.com, go get it from there." Alice's computer dutifully contacts Bug.com, which delivers an invisible image, so this transaction is not at all apparent to Alice. Effectively, the Spend.com site has tricked Alice into transmitting information from Spend.com and/or Alice's computer to Bug.com, without Alice's knowledge.
What information is carried by a Web bug?
1. The type of browser that fetched the Web bug image.
2. The time the Web bug was fetched.
3. The IP address of the computer that fetched the Web bug.
4. The URL of the main Web site.
5. The URL of the Web bug image located on the hidden Web site.
6. A previously-set cookie value.
Information types (1-2) are not necessarily such a big deal. However, (3-6) are more sensitive. The computer's IP address (3) can be traced by network providers, but this usually takes a fair amount of effort. By receiving (4), the hidden Web site learns where the user intended to browse. And the main Web site can control (5) to communicate any extra information it has through Alice's computer to the hidden Web site. Item (6) allows the hidden Web site to recognize the user's computer.
For example, suppose Alice creates an account at Spend.com, which contains a Web bug to Bug.com. During this process she enters her e-mail address alice@example.com. The Spend.com Web site could use a Web bug to transmit her address to Bug.com without Alice's knowledge. But the Spend.com site could send that information directly to Bug.com without involving Alice's computer at all!
Why is this important?
If Spend.com sent the infomation to Bug.com without going through Alice's computer, then all Bug.com could learn is that someone created a login at Spend.com with the e-mail address alice@example.com. Certainly Bug.com could add an e-mail address to their collection, but they would have no automatic way to associate the e-mail address with Alice's Web browser. When Alice visits other Web sites that also contain Bug.com Web bugs, they still wouldn't be able to deduce her e-mail address. Having given her e-mail address to Spend.com for the sole purpose of establishing an account there, Spend.com remains the only site that can recognize her and remember her e-mail address when she returns.
But if Spend.com uses a Web bug to transmit the information through Alice's computer to Bug.com, then Bug.com could arrange to communicate her e-mail address to many other Web sites. For example, when she later visits Splurge.com, it could get her e-mail address from Bug.com with very little effort. So in this case, even though Alice gave her e-mail address to Spend.com for the sole purpose of establishing an account there, she later discovers (without knowing why) that many other Web sites seem to suddenly know her e-mail address.
Can information other than e-mail addresses be shared between sites in this way?
Yes. Health interests, political affiliations, personally identifiable information, sexual disclosures: whatever is expressed at one Web site could be carried by a Web bug to many other Web sites.
Can a Web bug search a user's computer and extract data from it?
No. Web bugs only enable multiple sites to share information that they have collected using some other means, like enticing the user to enter the information into a Web form.
Can one Web site use a Web bug to extract data from another Web site against its will?
No. Of the three computers involved in a Web bug transaction, usually two of them have teamed up to communicate information about the third.
Are Web bugs able to carry any more information than ordinary third-party images such as banner advertisements?
No. But with banner advertisements, it's hard to know whether the information during the transaction has primary value or is just a side effect of delivering the advertisement to the user. But since Web bugs try to remain invisible, they must exist for the sake of the information exchange alone.
Why don’t Web site privacy policies mention Web bugs?
Good question. Web site privacy policies should disclose the use of Web bugs. In fact, the general practice of online profiling by third-party ad networks should be disclosed in privacy policies, but is rarely mentioned.
 Bugnosis
General FAQ Bugnosis
General FAQ
What is Bugnosis?
Bugnosis is a Web bug detector. As you surf the Web, it analyzes every page you visit and alerts you when it finds any Web bugs. With Bugnosis, you don’t have to be a code expert to tell when your browsing habits are being observed.
Who can use Bugnosis?
Bugnosis works only with the Internet Explorer (version 5.0 or greater) running on a Microsoft Windows operating system.
What happens when Bugnosis finds a Web bug?
Bugnosis runs a battery of tests on each suspicious graphic on a Web page when you first open it. If the program finds a possible Web bug, it alerts you with a sound ("uh-oh!") and gives you some details about the Web bug in a little window. It also makes visible the Web bugs hidden on the page, so you can see where they are placed.
You donít have to respond to any of this information
if you donít want to ó you can just keep surfing, or you can
stop and examine the details.
Can Bugnosis tell me if a Web bug is "good" or "bad"?
Not exactly, although the current battery of tests is a good first step in determining the purpose of any Web bug.
Generally speaking, a Web bug whose URL or cookie contains a large number, or a lot of random-looking text, is more likely to be used to track your movements than one whose URL or cookie consists mostly of jargon and abbreviations. The reason for this is that numbers and random-looking text are usually engineers’ first choices when they want to assign a tracking identifier to something (or someone). This is certainly not the only way to assign a tracking identifier, but it is one of the easiest. Because Web bugs are normally hidden by their small size, there is little motivation for an engineer to further obscure the identifier contained within it.
How can I find out what a Web bug is doing on a page?
It can be very hard to know the purpose of a Web bug, because they attempt to hide themselves, and are rarely mentioned in privacy policies.
The only way to really know is to ask the people who placed it there. For instance, if Bugnosis alerts you to a Web bug placed by visit.example.com, then you could try going to www.example.com and looking for a privacy policy that describes its use of Web bugs, or you could look for the e-mail address of a suitable contact, like a Chief Privacy Officer or a Webmaster.
Bugnosis can sometimes help in this search for a contact. It knows the Web pages for many (but not all) of the big corporate Web bug purveyors. If it identifies a Web bug for you and knows how to contact that site, it will show a little icon next to its analysis of the bug. Clicking
icon will bring up the siteís privacy policy.
Does Bugnosis use P3P (Platform for Privacy Preferences Project) to discover e-mail addresses or Web pages of the sites that place Web bugs?
No, not in this release.
Can Bugnosis block Web bugs from communicating information about me or my computer?
No. Bugnosis simply tells you who is watching.
Is there any way to block Web bugs?
You can try downloading an advertisement blocker like Guidescope, WebWasher or AdSubtract. Since
Web bugs are third-party content, most ad blockers will block Web
bugs, too. But they just don’t distinguish between images used
for transmitting advertisements and images used for communicating
information about users.
Can Bugnosis detect spyware or surveillance software such as keystroke or e-mail monitors?
No, Bugnosis only detects Web bugs embedded in Web pages.
Why isn't there a Netscape, Mozilla, Mac, or Opera version of Bugnosis?
Simple -- we don't have the time and expertise required to support
those platforms.
Can the Bugnosis sound ("uh oh") be turned off?
Oh yes. Right-click in the Bugnosis window to change its options, including sound and the appearance of your on-screen "bug."
The Web site contact icon only allows me to contact the site that placed the Web bug — the normally invisible third-party site. What about the site I intentionally visited, in which the Web bug was embedded? How do I contact them?
You’ll have to look around that site yourself to find a contact address or privacy policy. Bugnosis contains contact information for a few of the big Web bug placement companies, but these companies have many, many different clients — far too many to keep track of in Bugnosis’ database.
Is Bugnosis a proxy?
No, Bugnosis is a "browser extension" and can be used in addition to any proxies you may have installed.
Can Bugnosis detect Web bugs on secure (SSL/TLS/https) pages? How about Web bugs due to JavaScript code?
Yes! However, it's not able to make Web bugs
on secure pages visible. It will alert you to
their presence, but you won't see the cute bug image on the
page where the Web bug was placed.
Can Bugnosis detect Web bugs that I have received as e-mail?
No, sorry.
I’ve heard that images are only one way to send data with Web bugs. Does Bugnosis detect CSS bugs, script bugs, layer bugs, iframe bugs, etc.?
Sort of. Bugnosis will notice these elements
and might mark them as "suspicious". But it won't
identify them as Web bugs, because it's hard to decide
whether they were trying to be invisible or not.
This sounds like an arms race: Engineers design hidden Web bugs, you find out how to recognize and expose them, then they can use different hiding techniques. Is that right?
Well, yes. In practice, designers who employ Web
bugs are mostly trying to capture information and only
slightly trying to hide. But thereís a big difference
between a designer using Web bugs who thinks, "No one will
see this bug, itís not a big deal," and one who thinks, "Iím
going to hide this bug so well that Bugnosis wonít even see
it." The second designer is being actively hostile to usersí
preferences, and that's not very nice.
 Bugnosis 1.3 FAQ Bugnosis 1.3 FAQ
What happened to the email option? I want to
complain about a Web bug I found!
Many
sites provide automated privacy information with P3P, but
Bugnosis doesn't know how to read it yet. And it seems kind
of unfair for Bugnosis to make it easy to hassle those site
operators with email complaints when they've already gone to
effort to disclose their privacy practices. So the
email option is gone for now. You can always compose
your own email.
What files are installed with Bugnosis?
Just the files you see in its installation directory --
usually C:\Program files\Bugnosis.
 Bugnosis 1.1 FAQ Bugnosis 1.1 FAQ
I can't find the Bugnosis icon on my toolbar. Got any
tips for troubleshooting?
Start up Internet Explorer. If Bugnosis appeared
to install successfully but you still don't see the
 icon in your Internet Explorer
toolbar: icon in your Internet Explorer
toolbar:
  There might not be room on your toolbar for the Bugnosis
icon. If your toolbar is full, you'll see a little ">>"
symbol, meaning that some icons aren't being displayed.
Click on that and the little Bugnosis button might pop up
then.
There might not be room on your toolbar for the Bugnosis
icon. If your toolbar is full, you'll see a little ">>"
symbol, meaning that some icons aren't being displayed.
Click on that and the little Bugnosis button might pop up
then.
 Try
selecting View / Toolbars / Customize..., look for the
Bugnosis icon there, and add it to your current toolbar. Try
selecting View / Toolbars / Customize..., look for the
Bugnosis icon there, and add it to your current toolbar.
 Some
early versions of Internet Explorer 5.0 mistakenly call
everything "Radio", so if you see multiple Radio entries,
then one of them might actually be Bugnosis. Try enabling
it. Some
early versions of Internet Explorer 5.0 mistakenly call
everything "Radio", so if you see multiple Radio entries,
then one of them might actually be Bugnosis. Try enabling
it.
 Try rebooting. Some computers
seem to not show Bugnosis until they are rebooted. Try rebooting. Some computers
seem to not show Bugnosis until they are rebooted.
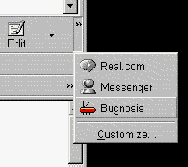
How can I find the "context menu" that controls Bugnosis? When you click on the Bugnosis icon in the toolbar, it either
shows or hides the Bugnosis "analysis window" -- a horizontal window
that takes up the bottom few lines of your Internet Explorer window.
The analysis window is where Bugnosis will tell you about Web bugs
that it finds. To find the Bugnosis context menu, you must first
make the Bugnosis analysis window appear, and then right-click
within that window. Note that right-clicking on the toolbar's
Bugnosis icon itself does not display the context menu.
Click here for a picture of the context menu. In the picture, the hourglass shows where the cursor was when the right mouse button was clicked.
I've heard that Bugnosis 1.1 is an ActiveX control.
Aren't ActiveX controls unsafe?
Depends on how they're used! Bugnosis 1.1 used
some ActiveX functionality as part of its installation
procedure, but 1.3 uses a different approach. Bugnosis was
never labeled "safe for scripting," in case you're worried
about that.
How can I uninstall Bugnosis
1.1?
 Right-click within the Bugnosis analysis window, and choose "uninstall" on the menu that appears.
Right-click within the Bugnosis analysis window, and choose "uninstall" on the menu that appears.
 Another approach is to install and then uninstall Bugnosis
1.3; it should remove both versions on the way out.
Another approach is to install and then uninstall Bugnosis
1.3; it should remove both versions on the way out.
If
these techniques don't work for you, see some of the other options below.
Can I uninstall Bugnosis 1.1 with BHO Cop?
Yes, PC Magazine's "BHO Cop" does a fine job of
managing Bugnosis (and other Browser Helper Objects). You'll have to install BHO cop, but it's a good little program and it's free too. Click here for more information and the download link.
How can I manually uninstall Bugnosis 1.1?
You can try two
manual procedures. The simplest is to click the Windows
"Start" button, choose Run, type uninstallbugnosis,
and press enter. If that doesn't seem to work, click Start, choose
Run, type command (cmd if your computer is running NT,
2000, or XP) and press enter. In the command window that appears, type these
three lines, pressing enter after each one:
cd "%WINDIR%\downloaded program files
rundll32 webbug.dll,UninstallBugnosis
exit
Be very careful to type the punctuation and capitalization exactly as shown. As a check, note that the first line ("cd ...") contains
three space characters, and the second line contains only one space character.
What files are installed with Bugnosis?
The Bugnosis installation puts files in
\windows\Downloaded Program
Files\ and \windows\system\ (on Windows NT, 2000, and XP,
\winnt\Downloaded
Program Files\ and \winnt\system\)
In Downloaded Program Files:
webbug.dll, webbug.inf, current-ruleset-1.2.xml
(or similar)
These files constitute Bugnosis proper. Note, however, that
Downloaded Program Files is a special directory, and Windows
Explorer will not show all of these files. You can use dir at
the command prompt (command or cmd) in order to view and
manipulate the files.
Bugnosis also installs MSXML3, which goes in your
\windows\system (or \winnt\system) directory as the files
msxml3.dll, msxml3r.dll, msxml3a.dll. MSXML3 is
Microsoft's XML parser; Bugnosis relies on it to handle some internal bookkeeping.
Can I just remove some of these files if I want to uninstall?
The most important file is webbug.dll. If Internet
Explorer cannot locate this file when it starts up, Bugnosis will not
run. So, renaming this file will effectively disconnect Bugnosis,
even though Internet Explorer will still try to look for it. For
instance, click Start, choose Run, type command (cmd if
your computer is running NT, 2000, or XP) and press enter. In the command
window that appears, type these three lines, pressing enter after each
one:
cd "%WINDIR%\downloaded program files
ren webbug.dll webbug-old.dll
exit
Can I use regedit to uninstall?
If you're comfortable with regedit, then you can delete the key
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{3A6514CD-A457-11D4-8AF3-000102686B79}. The next time Internet Explorer starts up, it won't even try to load Bugnosis.
Why are there so many questions about uninstalling?
The installation/uninstallation of Bugnosis 1.1 was not
its strongest point, and we sure don't like software that's
hard to uninstall either. Happily, Bugnosis 1.3 is
much cleaner in this regard.
|
|
|